compliance-operator: Scanner fails to detect remidiated auditd rules
I have been testing manually fixing issues reported by the compliance-operator using custom machineconfigs. So far I have tested manual fixes to /etc/ssh/sshd_config and /etc/audit/auditd.conf and these have worked fine.
One potential issue I have noticed that the scanner can’t seem to detect fixes I make to the auditd rules.
This was the process I went through when I encountered this issue:
- Created a machine config that creates a new audit rules file
/etc/audit/rules.d/test.rules - Waited for the nodes to apply this change
- SSHed in to on of the nodes and confirmed the file was installed successfully with correct permissions (0600). Also confirmed that the rules had been successfully copied by the audit daemon to /etc/audit/audit.rules.
- Ran a new scan by creating a new compliancesuite CR
- I get similar output to for all the fixed audit rules:
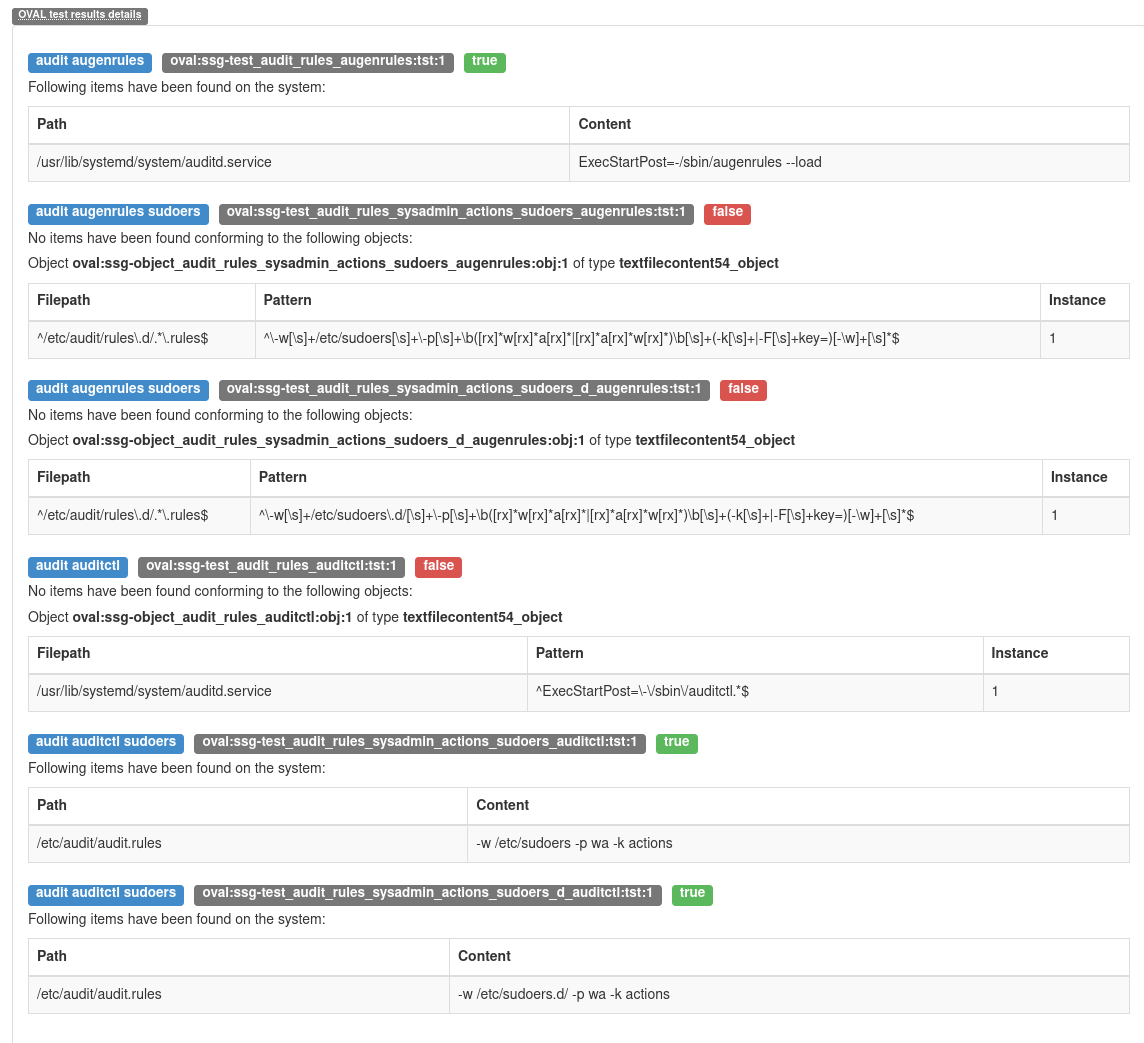
You can see here that it is correctly detecting the rules in /etc/audit/audit.rules but not in /etc/audit/rules.d/test.rules
I have even tried downloading and running the remidation playbook and it applies no changes:
$ ansible-playbook -u core playbook.yaml -b -i "worker1.fqdn,"
PLAY [all] *************************************************************************************
TASK [Gathering Facts] *************************************************************************
[WARNING]: Distribution redhat 4.3 on host worker1.fqdn should use /usr/bin/python,
but is using /usr/libexec/platform-python, since the discovered platform python interpreter was
not present. See
https://docs.ansible.com/ansible/2.9/reference_appendices/interpreter_discovery.html for more
information.
ok: [worker1.fqdn]
TASK [Search /etc/audit/rules.d for audit rule entries for sysadmin actions] *******************
ok: [worker1.fqdn]
TASK [Use /etc/audit/rules.d/actions.rules as the recipient for the rule] **********************
skipping: [worker1.fqdn]
TASK [Use matched file as the recipient for the rule] ******************************************
ok: [worker1.fqdn]
TASK [Inserts/replaces audit rule for /etc/sudoers rule in rules.d] ****************************
ok: [worker1.fqdn]
TASK [Inserts/replaces audit rule for /etc/sudoers.d rule in rules.d] **************************
ok: [worker1.fqdn]
TASK [Inserts/replaces audit rule for /etc/sudoers in audit.rules] *****************************
ok: [worker1.fqdn]
TASK [Inserts/replaces audit rule for /etc/sudoers.d in audit.rules] ***************************
ok: [worker1fqdn]
PLAY RECAP *************************************************************************************
worker1.fqdn : ok=7 changed=0 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
About this issue
- Original URL
- State: closed
- Created 4 years ago
- Comments: 19 (5 by maintainers)
Commits related to this issue
- Merge pull request #202 from ComplianceAsCode/release-v0.1.60 Release v0.1.60 — committed to jhrozek/compliance-operator-1 by openshift-merge-robot a year ago
Great, let me close the issue, then. Thank you for reporting back.
@yuumasato I have tested with @jhrozek’s new image and the scanner is now detecting the fixed audit rules. Thank you very much for this fix.
That’s what I thought too, but from the openscap report output it looks like there it’s looking for a regex match in files within the rules.d directory:
Here is a tarball of the un-base64’d decompressed ARF files from some of my scans. The first one is using a custom profile I am attempting to create and the second one is using the example compliancesuite from the repo. I have also attached my machineconfig that I used to make the remediations:
compliance-operator-issue-202.tar.gz
By the way, the custom profile I was using for one of the scans is here: https://github.com/jaedolph/content/blob/e8-ocp4/ocp4/profiles/e8.profile Container image build for the profile is here: https://quay.io/repository/jaedolph/ocp4-openscap-content?tab=tags