amplify-js: 'cannot get guest credentials' error on clicking Sign Out button in Greetings component
Do you want to request a feature or report a bug? Bug
What is the current behavior?
When signed in as a Cognito user, clicking “Sign Out” in the default <Greetings> component throws an error, as shown:

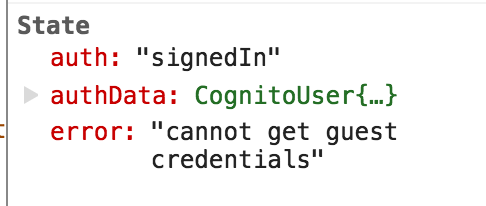
With the corresponding React state (still showing auth: signedIn and my signed-in authData):
After reloading the page, I am successfully shown as signed out (the <SignIn> component renders).
What is the expected behavior?
Clicking Sign Out in the default Greetings component should show the “Sign In” UI, with no errors.
The new error appears to be from the new catching logic here (it was previously always resolved): https://github.com/aws/aws-amplify/commit/1e8a497d6746b4e0f877738568a36ccfee757691#diff-0dac56aa728020901cdf9a90ec3ee802R844
Which versions of Amplify, and which browser / OS are affected by this issue? Did this work in previous versions?
I’m using aws-amplify@0.2.12, aws-amplify-react@0.1.37.
My component has an <Authenticator> with some custom children, and options <Authenticator hideDefault={true} theme={theme}> (although I tested it with and without hideDefault).
The “sign out” button worked in previous aws-amplify versions (although those had other issues, hence my update).
CC @powerful23
About this issue
- Original URL
- State: closed
- Created 6 years ago
- Comments: 21 (9 by maintainers)
@tyson-kubota It’s not a requirement for using those React components. I think the library shouldn’t send errors to users if there is no guest credential available. We can log this in the background saying there is no guest credential available. Other categories like Analytics will check AWS credentials so when they find there is no credentials available they will stop working.
I’m using
1.0.2@powerful23 and I’m still getting that error@powerful23 this still occures for me when the pool doesn’t allow the unauthenticated access, can you verify this bug is still existing?
@tyson-kubota Seems like you didn’t allow unauthenticated access into your identity pool.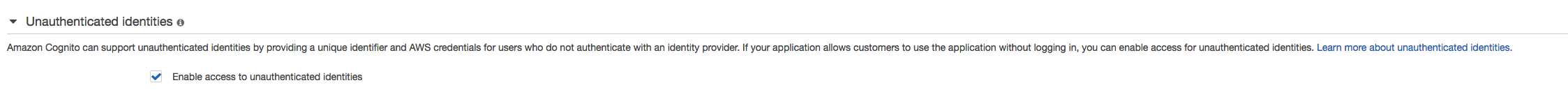
For now you can either turn on that or we can make a patch for that issue