mold: miscompilation for rust target i686-unknown-linux-musl
Mold v1.0.3 miscompiles call targets constructed from this sample program:
pub fn main() {
unsafe {
let x: usize = 0x12340000;
let f: extern "C" fn() = std::mem::transmute(x);
f();
}
}
According to all the documents I could find, this should not be UB in Rust, but a valid way to create a function call from a known address.
call 0x12340000 ; expected call
call 0x1233ffff ; actual call
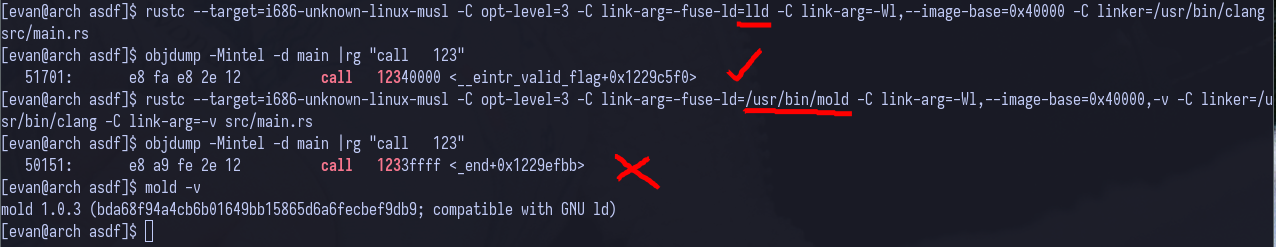
In the image, the image-base option is not needed to reproduce the issue. I just wanted to show the instruction encoding differences between lld and mold from the same source EIP address.
About this issue
- Original URL
- State: closed
- Created 2 years ago
- Comments: 15 (8 by maintainers)
Yes, that’s useful. Thanks. It looks like mold miscomputes a relocation value for the special case that a relocation refers
SHN_UNDEF. I’ll fix the issue before the next release.It should be fixed in the above commit. Thank you for reporting the issue to me.
Ah yes, that was it! I was just removing the final binary.
And I can confirm now the call target is correct ❤️
Thanks for investigating this, and thanks for mold 😃