prisma: Error: The certificate was not trusted
Hello, I’ve got this error today with latest alpha:
prisma2@2.0.0-alpha.281, binary version: c55e482a7a27ec30ea41b074ffb3de8a1a40c36e
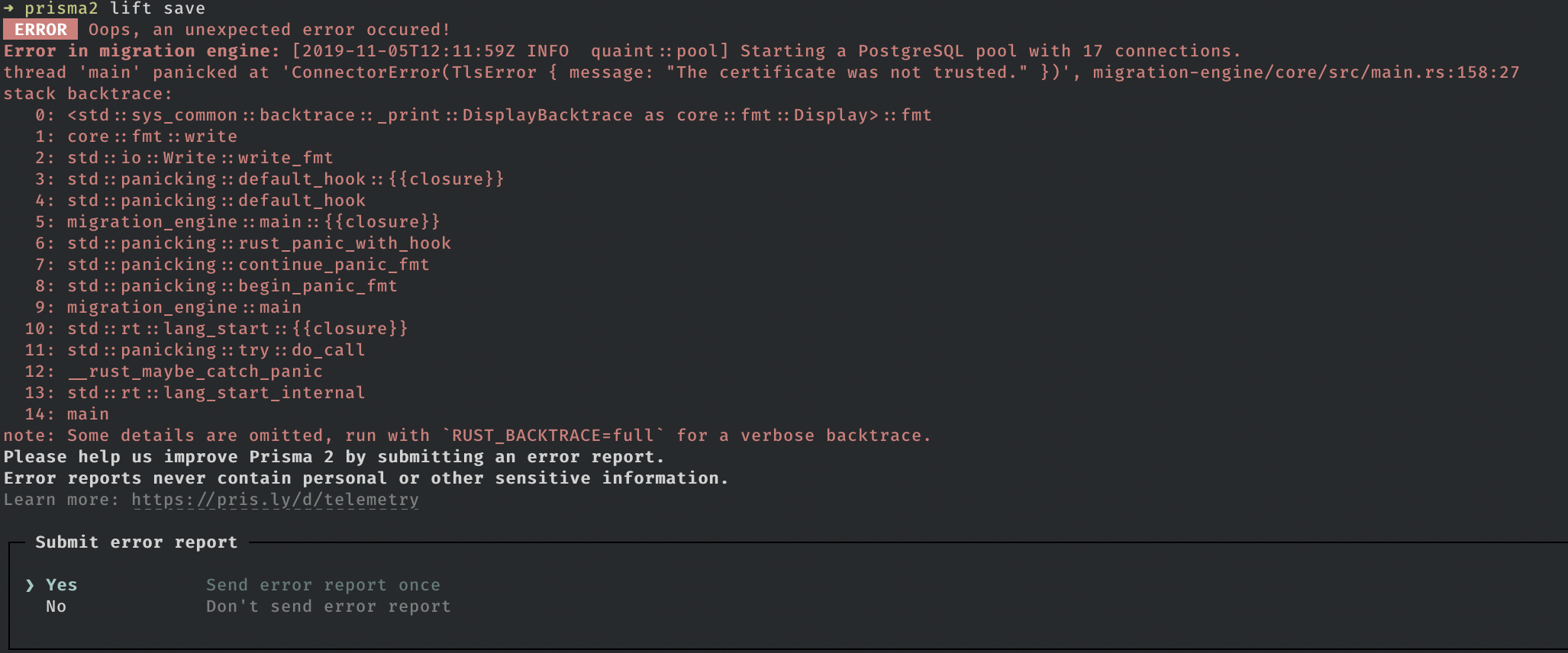
PS: I’m with sslmode=prefer and report id 457
About this issue
- Original URL
- State: closed
- Created 5 years ago
- Reactions: 1
- Comments: 28 (14 by maintainers)
Adding
sslaccept=accept_invalid_certsto your datasource url should work for now@janpio , @pantharshit00
prisma2 lift saveproduces the error aboveThe same three steps with a local postgresql database work fine.
This is fixed upstream, the change should make it in preview 18 😃 More context in https://github.com/prisma/specs/issues/325
I can confirm this bug in
prisma2@2.0.0-preview016, binary version: 377e2db71bae5da19d0090558c8819ff57dfdfc6Thanks for the reproduction steps @iherger 😃
@janpio Could we get a clarification on this?
I have just tried this approach:
prisma2 generate– works without any problemprisma2 generate(on my local) – seen the errorsslaccept=accept_invalid_certsand call the command again – now it works fine, the remote database were generated.So IMHO the problem is still there
Encountering the same issue with a postgres database hosted on heroku. Adding
sslaccept=accept_invalid_certsto the connection url fixed it.Yes, we implemented passing custom certificates for postgres connections a few weeks ago and I think that’s when the decision was made.
I spent a lot of time investigating this, and the conclusion is that what we are doing is not buggy, but much stricter than most other postgres clients. We will relax the current behaviour a bit (otherwise you would have to pass certificate files to the postgres connection in nearly every scenario). I will keep this issue up to date.