prisma: Error: P1011: Error opening a TLS connection: Internal error
As a result of: https://prisma.slack.com/archives/CKQTGR6T0/p1605611171317000
I tried migrating my database hosted on Google Cloud SQL and got the following error:
I am not using SSL.
This is the format of the connection string I am using: postgresql://username:password@IP:Port/database
Connecting to the database with psql with the same connection string works fine.

Prisma version: 2.11.0 (But the error also occurred with 2.10.0) OS: MacOS BigSur
About this issue
- Original URL
- State: closed
- Created 4 years ago
- Reactions: 9
- Comments: 18 (6 by maintainers)
I was able to resolve this issue by adding:
trustServerCertificate=true;
to the DATABASE_URL
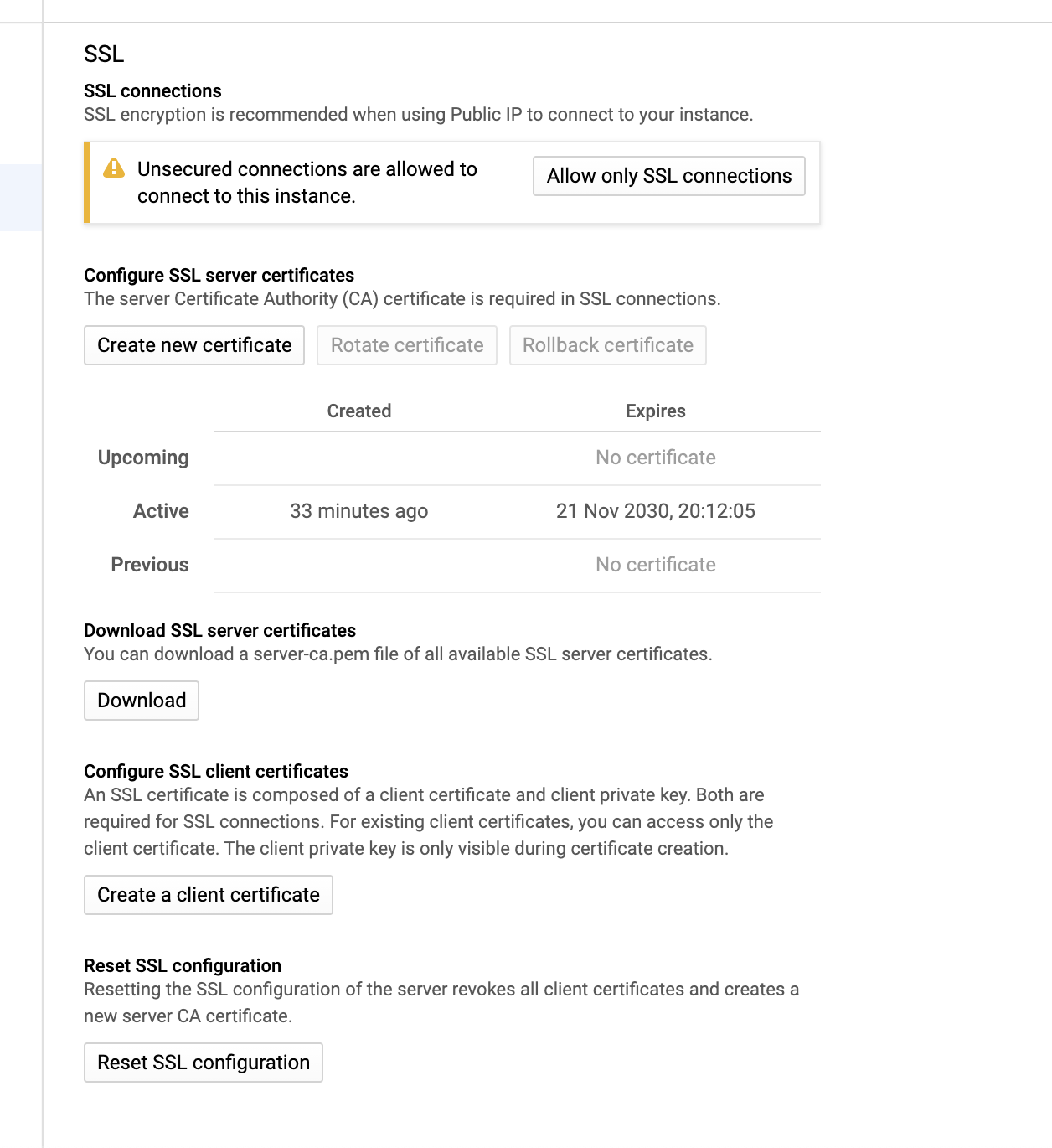
I also bypassed the issue by issuing a new certificate (Create new certificate) and rotating it (Rotate certificate):
+1 I am seeing this as well after upgrading to Big Sur. Happened on Prisma versions 2.5.1, 2.10.0, and 2.11.0.
I am unable to reproduce this on macOS Big Sur 11.0.1 and NodeJS v14.15.1 on an Intel based 2018 Macbook Pro.
I tried both
devandlatesttag2.11and2.12.0-dev.52.These are the connection properties that I am using: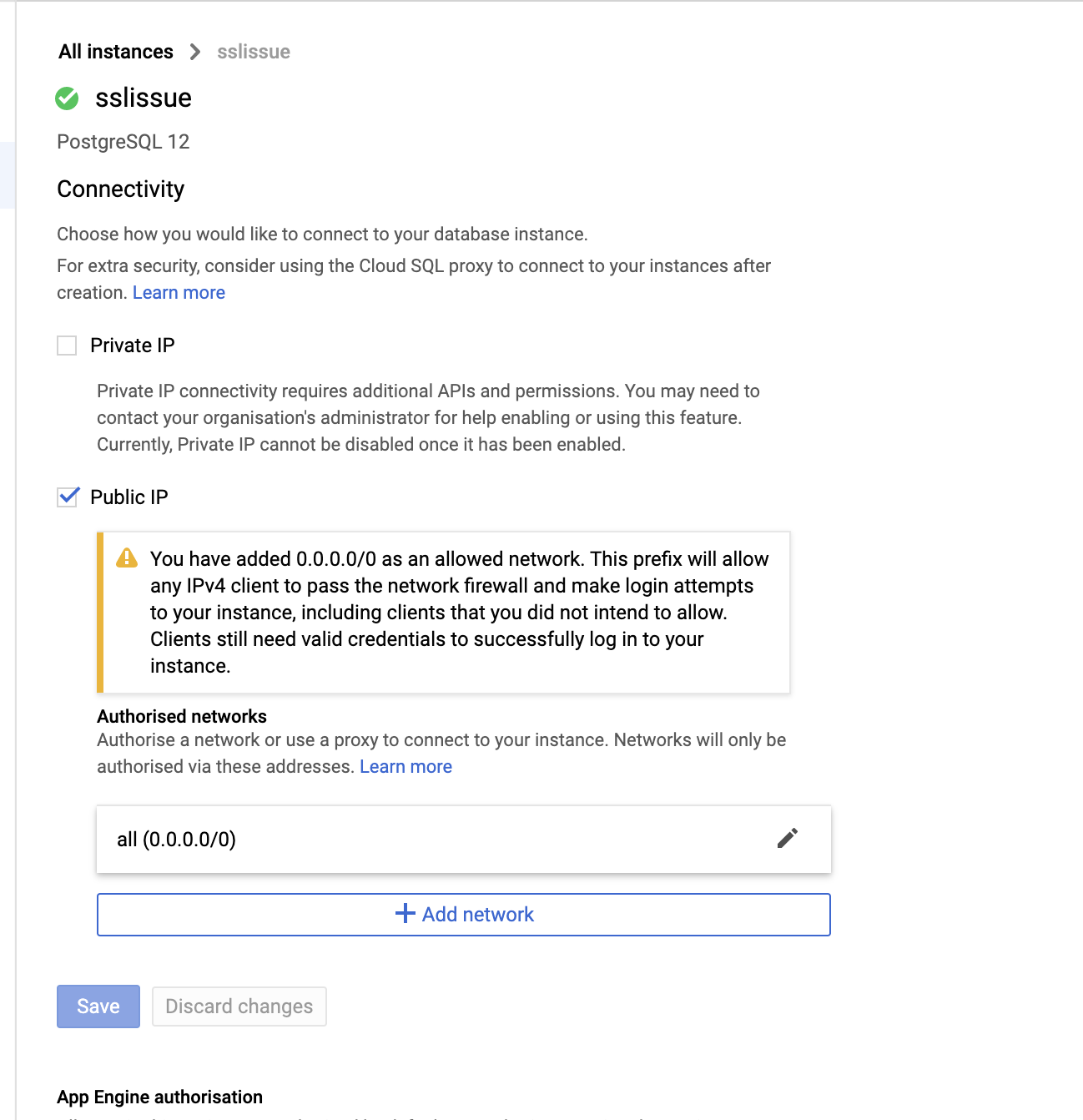
Thanks for looking into it further @pantharshit00. Appreciate how the Prisma team has been responsive on this issue.
So I think I have a resolution for those still affected. If you simply create a clone of your Cloud SQL service, and use the new IP details you’ll find that you can create a prisma connection just fine.
So I guess GCP made a change to our existing services that caused problems, and creating new services fixes it. Or this could be some kind of ongoing Big Sur issue that might come up again? Doesn’t feel like a Prisma specific issue though.
@ChipClark Please open a new issue with a minimal reproduction.
It should not as long as you are passing the correct certificates. Also, workaround is documented by GCP itself I am pretty confident that it is safe.
I cannot speak for your use case, but ours were really simple, and I had nothing more to do than what I described.
Looks like this can be closed as it sounds like a GCP issue that can be solved by rotating the server certificate and recreating the client certificates. 🎊
I just hit this issue myself. it seems to be something on the GCP side: https://cloud.google.com/sql/docs/troubleshooting