pomerium: OCSP staple sometimes missing
What happened?
Note I cannot reproduce this issue but I’m pretty certain it happened.
It looks like in some cases the HTTPS response does not contain OCSP staple result, which conflicts with OCSP Must-Staple and cause HTTPS connection to fail.
This only happened to one of my routes. Chrome would fail to connect. When I test the server using ssllabs.com it returned A+ with warning that there’s no OCSP stapling in the response.
Restart the server seems to have fixed the issue. I do notice the route’s certificate was recently renewed on Feb 19 but not sure if this is related.
What did you expect to happen?
How’d it happen?
- Ran
x - Clicked
y - Saw error
z
What’s your environment like?
- Pomerium version (retrieve with
pomerium --version): 0.13.0 - Server Operating System/Architecture/Cloud:
What’s your config.yaml?
# Paste your configs here
# Be sure to scrub any sensitive values
What did you see in the logs?
# Paste your logs here.
# Be sure to scrub any sensitive values
Additional context
Add any other context about the problem here.
About this issue
- Original URL
- State: closed
- Created 3 years ago
- Comments: 17 (8 by maintainers)
Thanks for opening this issue. Until now I’ve been unable to find the cause of the Chrome error:
ERR_SSL_VERSION_OR_CIPHER_MISMATCHand Firefox:SSL_ERROR_NO_CYPHER_OVERLAPRunning the ssllabs.com test, I’m getting the same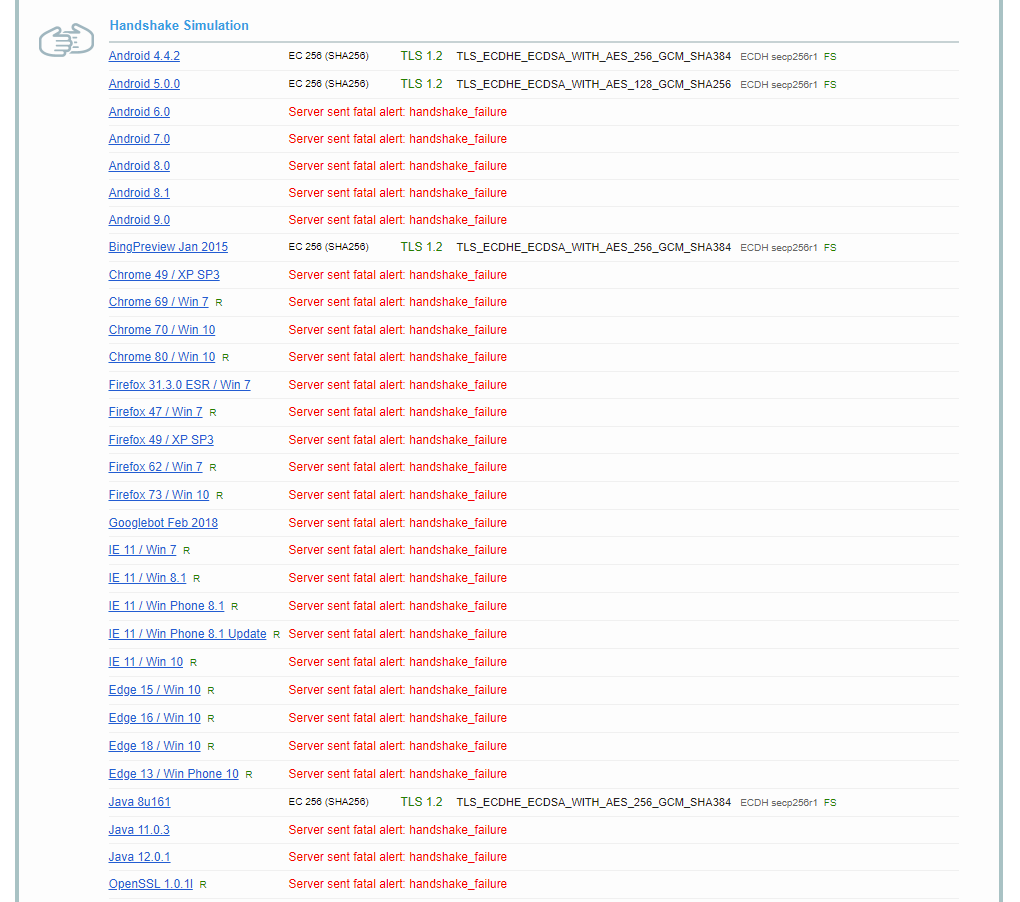
However for me, the error is completely persistent and predictably happens within 1-2 weeks of running Pomerium via docker-compose. I cannot get the same logs as others here, the only thing I see in the debug output is:
If needed, I can provide access to a server that has the issue, but will take 1-2 weeks to setup.
With the specific error,
TLS error: 268435589being zero-hits on google.Restarting the affected container immediately allows connections to pass again in Chrome and Firefox.
Is there a workaround for this other than regular scheduling of
proxyandauthenticatecontainers to restart? Unfortunately my healthcheck withcurldoes not reject the missing OSCP stapling, so I’m also a bit at a loss of how exactly to detect this problem.This also still happen to me. I decide to post my full configuration (with information redacted) in case it can help the investigation.
docker-compose config (in jsonnet format):
pomerium.yaml file:
And it happened again. ERR_SSL_VERSION_OR_CIPHER_MISMATCH SSLlabs reports: This server certificate supports OCSP must staple but OCSP response is not stapled. And a lot of handshake failures: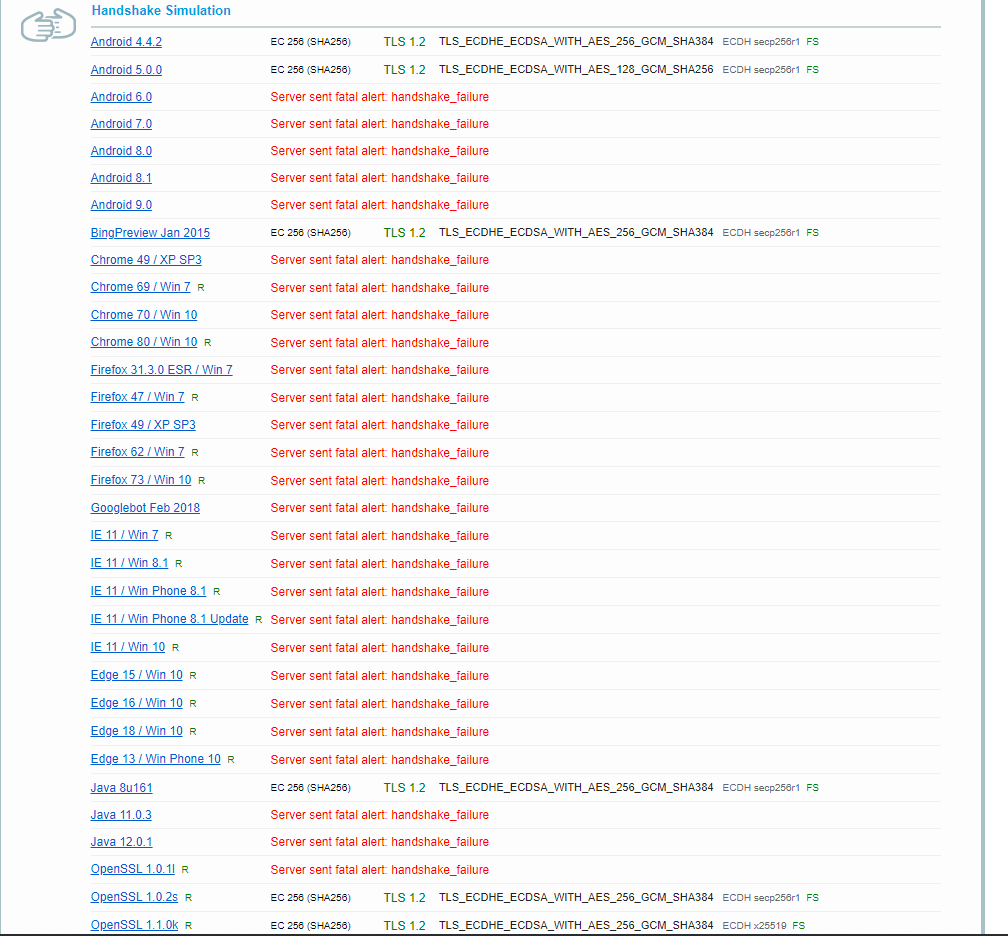
Even with POMERIUM_DEBUG TRUE, I dont find anything in the pomerium logs regarding the failed requests. I will leave it in this state, if something needs to be tested.