core: NAT reflection doesn't appear to be working
Not sure if this is a bug or not. I’m running 19.7.5_5. So I have my XMPP server on an inside subnet, and I’ve got the port forward working…at least from the outside.
So outside my LAN, people can reach my chat server and authenticate using the DDNS I have setup. No issue there. However, from inside the LAN I can’t use the DDNS address. I have to specify the internal IP of the server to use the chat when I’m at home. I can only assume this has something to do with the port forwarding, but I’m not sure what it would be.
I don’t see anything in the live logs in terms of traffic being blocked or anything when I try to connect using the DDNS address. I can see the traffic being allowed, or at least it seems to be.
Inside Oct 16 18:07:36 192.168.50.71:62192 10.5.7.18:5222 tcp let out anything from firewall host itself Inside Oct 16 18:07:36 192.168.50.71:62192 10.5.7.18:5222 tcp
Not sure I know how to read the state table but I do see this
192.168.50.27:49436 -> 10.5.7.18:5222 SYN_SENT:CLOSED

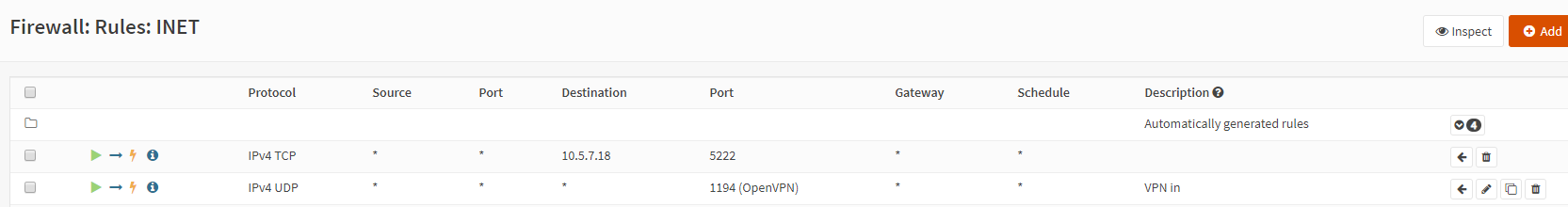

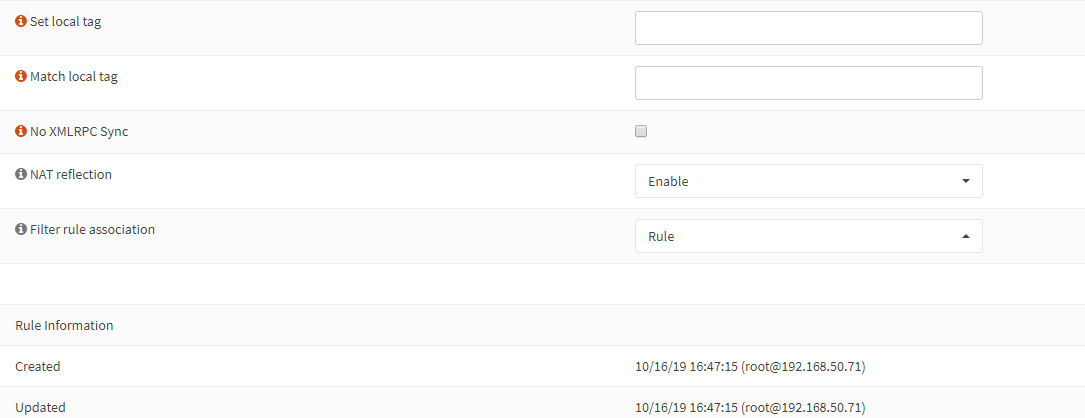
I already have “Reflection for port forwards” and “Automatic outbound NAT for reflection” enabled. I also reset the state tables but no change.
Any help is appreciated. Thank you!
About this issue
- Original URL
- State: closed
- Created 5 years ago
- Reactions: 1
- Comments: 20 (7 by maintainers)
Has been testing NAT reflection on my env like this. I guess this is called double NAT which causes the issue.
WAN <> iptables <> opnsense <> LANDetailed working setting: go to
Firewall / Settings / Advancedcheck these box(optional) go to
Firewall / Aliasesadd new recordgo to
Firewall / NAT / Port Forwardadd new recordHope this help
Firewall: Settings: Advanced Reflection for port forwards Y Automatic outbound NAT for Reflection Y
This setup works fine.
@VooPoc What you posted will not work It should be
Interface: LAN Source: LAN net Destination Address: WAN net Destination Port: Your server port Translation/target: Internal Server Address and Port
The rule says “If traffic from inside bound for the public ip/port is found, redirect that traffic to the internal host and port”
And yes - “NAT Reflection” on OPNsense is a dumpster fire. Better off just buildiongf manual rules.
Any update on this?