keycloak: Get UserInfo return 401 Unauthorized
Before reporting an issue
- I have searched existing issues
- I have reproduced the issue with the latest release
Area
oidc
Describe the bug
After service account authenticated via client_credential flow, I send a request with its access_token to userinfo_endpoint, but Keycloak server return 401 Unauthorized
Version
20.0
Expected behavior
Keycloak should return 200 OK with user information as the same as normal user
Actual behavior
401 Unauthorized
How to Reproduce?
docker compose up -dversion: '3' services: keycloak: image: quay.io/keycloak/keycloak:20.0 command: [start-dev] environment: KEYCLOAK_ADMIN: admin KEYCLOAK_ADMIN_PASSWORD: SuperSecr3t ports: - 8080:8080 volumes: - keycloak_data:/opt/keycloak/data volumes: keycloak_data: driver: local- Create new realm
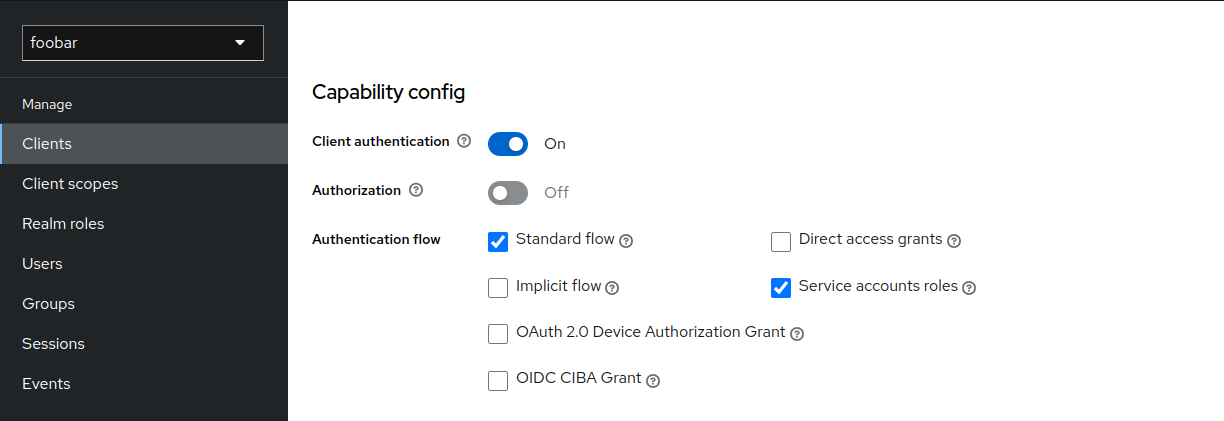
- Create new OIDC client and enable
Service accounts roles- Authenticate using service account
curl --location --request POST 'http://localhost:8080/realms/<realm>/protocol/openid-connect/token' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --data-urlencode 'grant_type=client_credentials' \ --data-urlencode 'client_id=<client_id>' \ --data-urlencode 'client_secret=<client_secret>'- Get userinfo:
bash curl --location --request GET 'http://localhost:8080/realms/<realm>/protocol/openid-connect/userinfo' \ --header 'Authorization: Bearer <access_token>'
Anything else?
No response
About this issue
- Original URL
- State: closed
- Created a year ago
- Comments: 19 (5 by maintainers)
This change was documented in the migration guide https://www.keycloak.org/docs/latest/upgrading/index.html#userinfo-endpoint-changes .
In shortcut, UserInfo is OIDC specific endpoint when service-accounts (client credentials) is OAuth2 thing. So the fact that UserInfo works just for the access tokens using
scope=openidis completely fine to me. Also it is fine that service-accounts don’t use thisscope=openidby default and hence service-account access tokens don’t work with UserInfo by default.In fact, it is bit strange that someone even uses UserInfo endpoint (which is supposed to be for “real users”), for “Service accounts” (which are not real users). Using token-introspection endpoint looks like better option for service-accounts.
@pedroigor @rmartinc WDYT guys? Do we just close this or do we want to add some “backward compatibility option” for stick the the previous behaviour? If we provide backward compatibility, do we add it to the OIDC client configuration to other
Open ID Connect Compatibility Modesoptions?Hi, Added scope=openid in the /token endpoint and getting the access token added with the scope mentioned. But when trying to hit /userinfo with the access token, still getting 401 unAuthorized
Can someone help over here?
If someone still search for compatibility: Create client scope ‘openid’ in realm and add it as default assigned type in your OAuth clients, no need to request it on login.
Adding to Keycloak 22 for now as it is related to backwards compatibility.
I believe this is an intended effect of this change - you need to add a scope called
openidto the client.Any keycloak 19 version does not contain https://github.com/keycloak/keycloak/pull/14237 and therefore does not have this problem
The issue with that is that some OAuth clients don‘t like when the openid scope suddenly appears in the authorized scopes, which is why I‘d still like to see a compact option for keycloak 22. For now I‘m stuck on keycloak 19 because of this issue.
I found if the client side requests the
openidscope explicitly in login, even without adding theopenidscope to keycloak client, theopenidwill be included in issued token and the/userinfowill works also.So it seems that adding
openidto the client’ request scope is also a workaround. some library likekeycloak-jsalready did this and some are not, like OAuth in swaggermeet the same problem after upgrade to 21.0.1
I think we need to add the
openidas a default scope to each client when make this changeIt may sound stupid if everyone need to manually add the
openidclient scope and add it to each client to get things workYou have to create a client scope called
openidand request it.Having the same problem. Unable to use
/userinfoendpoint. Furthermore, I also tried to add theopenidscope to the client. Getting the same error:I think keycloak should provide a (compatibility?) option to restore the old (pre-v20) behaviour. (Allow user info to be queried without explicitly requesting the openid scope in OAuth flows) See also #16168 and #16610