keycloak: Admin console not loading and hostname related issues
Describe the bug
It seems the new admin console doesn’t load properly under some configurations, and this has been reported many times in different issues.
This is serving as an umbrella issue to collect all the reported issues.
When reporting issues please use the hostname-debug tool to help us figure out what’s going on:
- Start Keycloak with the
--hostname-debug=trueoption - After starting Keycloak open
KEYCLOAK_BASE_URL/realms/master/hostname-debug - Copy/paste the results to comments below, this will allow us to figure out your configuration, reverse proxy settings, and the results. If URLs are sensitive please replace with example URLs
Reported issues:
- https://github.com/keycloak/keycloak/issues/14662
- https://github.com/keycloak/keycloak/issues/14586
- https://github.com/keycloak/keycloak/issues/14668
- https://github.com/keycloak/keycloak/issues/14637
- https://github.com/keycloak/keycloak/issues/14242
- https://github.com/keycloak/keycloak/issues/14135
- https://github.com/keycloak/keycloak/issues/13665
- https://github.com/keycloak/keycloak/issues/14628
- https://github.com/keycloak/keycloak/issues/14812
- https://github.com/keycloak/keycloak/issues/15375
- https://github.com/keycloak/keycloak/issues/12766
- https://github.com/keycloak/keycloak/issues/17137
- https://github.com/keycloak/keycloak/issues/17586
- https://github.com/keycloak/keycloak/issues/19590
- https://github.com/keycloak/keycloak/issues/12823
- https://github.com/keycloak/keycloak/issues/19951
- https://github.com/keycloak/keycloak/issues/19821
- https://github.com/keycloak/keycloak/issues/20145
- https://github.com/keycloak/keycloak/issues/20178
- https://github.com/keycloak/keycloak/issues/20775
- https://github.com/keycloak/keycloak/issues/21581
- https://github.com/keycloak/keycloak/issues/21670
- https://github.com/keycloak/keycloak/issues/21882
- https://github.com/keycloak/keycloak/issues/21784
- https://github.com/keycloak/keycloak/issues/22088
- https://github.com/keycloak/keycloak/issues/23000
- https://github.com/keycloak/keycloak/issues/23822
- https://github.com/keycloak/keycloak/issues/23788
- https://github.com/keycloak/keycloak/issues/24738
- https://github.com/keycloak/keycloak/issues/25027
- https://github.com/keycloak/keycloak/issues/25754
Follow-up:
About this issue
- Original URL
- State: open
- Created 2 years ago
- Reactions: 7
- Comments: 66 (11 by maintainers)
Just because I spent hours trying get it to work, it may help others. I read most of the linked tickets above to find the cause. Thanks for summarising the issues here! Once I figured it out, migrating from 16 to 19 was super easy.
During the testing on staging I ran into 403 (redirect_uri) and 404 (/resources) errors, because of wrong URLs, so mostly because of my stupidity. I literally tried all ENV var combinations I could think of. In the end I had mistakenly added the
/adminto the admin URL.Using bitnami/keycloak chart, setting the following:
KC_HOSTNAME_URLandKC_HOSTNAME_ADMIN_URLto the same value, including port, likehttps://my.domain:8443/, include/auth/for backwards compatibility. No other KC_HOSTNAME* variables used.httpRelativePath: "/auth/"for backwards compatibility (mind the trailing/)proxy: edgecache.enabled: truefor infinispan (if using replicaCount > 1)proxyAddressForwarding, oldcacheandserviceDiscoverysections and envKEYCLOAK_FRONTEND_URLOnce I got my stage setup up and running, upgrading production worked like a charm from chart version 7 to 10.
I found the issue with my setup:
I tried every combinations of the above.
It’s a Bug present in all recent versions of KeyCloak.
KeyCloak can not handle default ports!
I had to specify
hostname-admin-urlandhostname-urlwithout the port!Do not follow the documentation! https://www.keycloak.org/server/all-config
Adding the port to the URL, when using default ports (80 or 443), breaks KeyCloak.
Apparently, KeyCloak consider “https://domain.com:443” to be a different URL from “https://domain.com” and refuse the request without giving any error messages.
If the

hostname-admin-urlor thehostname-urlis not specified in the config, KeyCloak craft one for you, and includes the port in the URL, breaking itself.To get everything working on Keycloak 22 behind a TLS-terminating ingress in a Kubernetes cluster, we had to set the following environment variables:
Setting KC_HOSTNAME_ADMIN to the same value as KC_HOSTNAME doesn’t help, as it seems like for the admin console the strict-https is ignored, and the hostname-debug tool also shows it failing as an http-URL.
Keycloak 21 was fully functional with just setting KC_HOSTNAME explicitly, after the update to 22 everything broke down without the above settings. The admin console complained about invalid redirect uris, issued tokens were invalid etc.
It seems like there were several hidden changes to how these settings are handled between 21 and 22, and they should have been documented in the release notes and migration guide.
facing the similar issue, I am using keycloak 21.1.1 and deploying in EKS. accessing through kong gateway.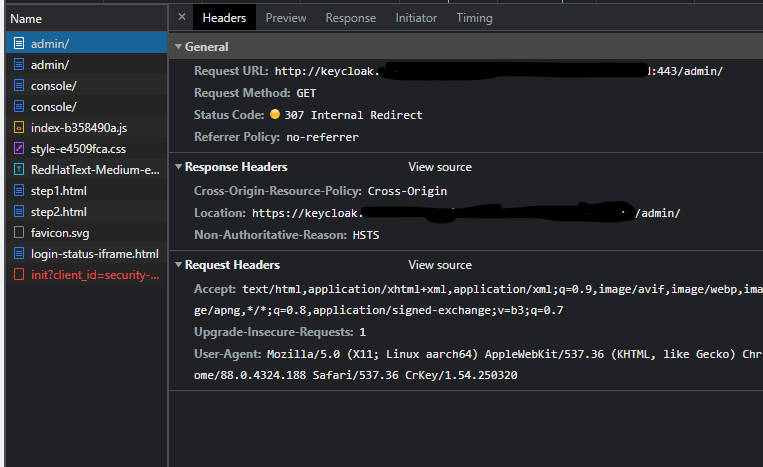
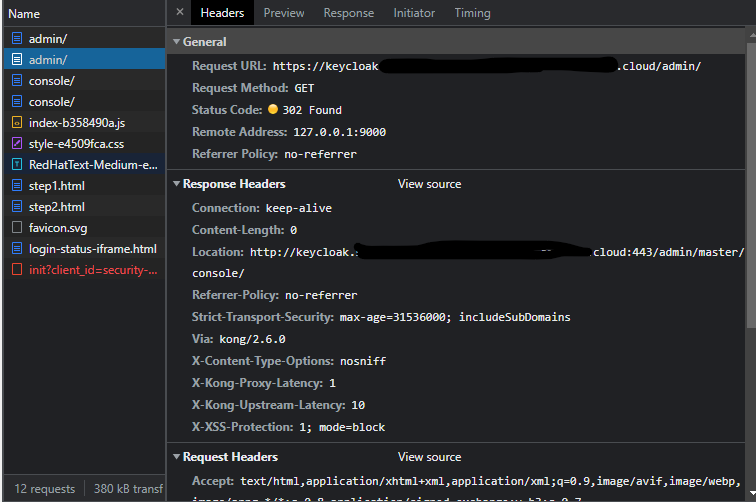
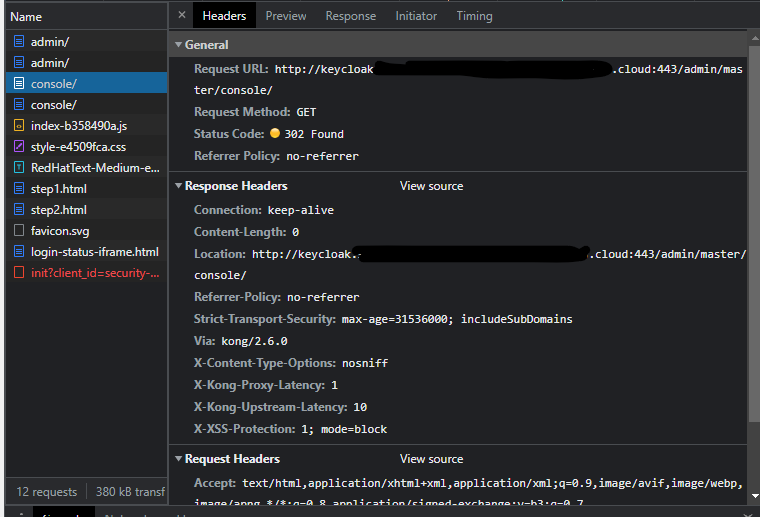
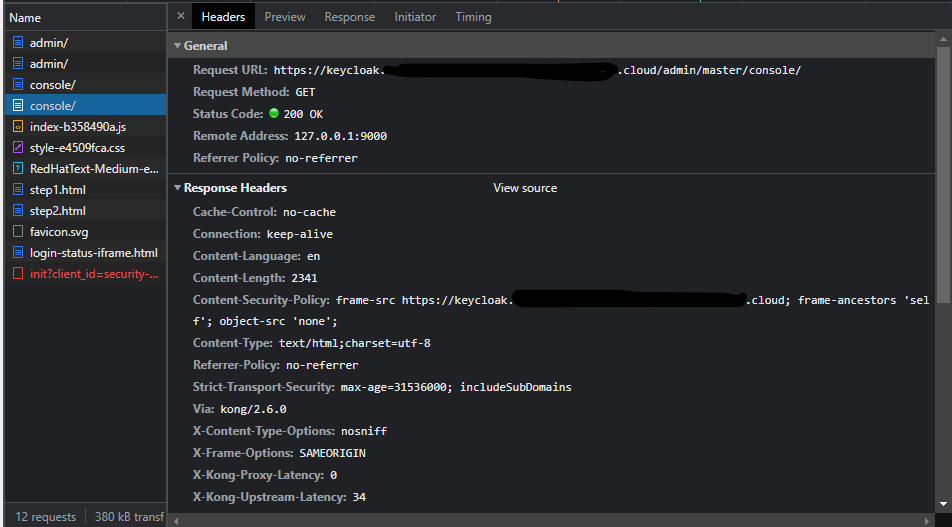

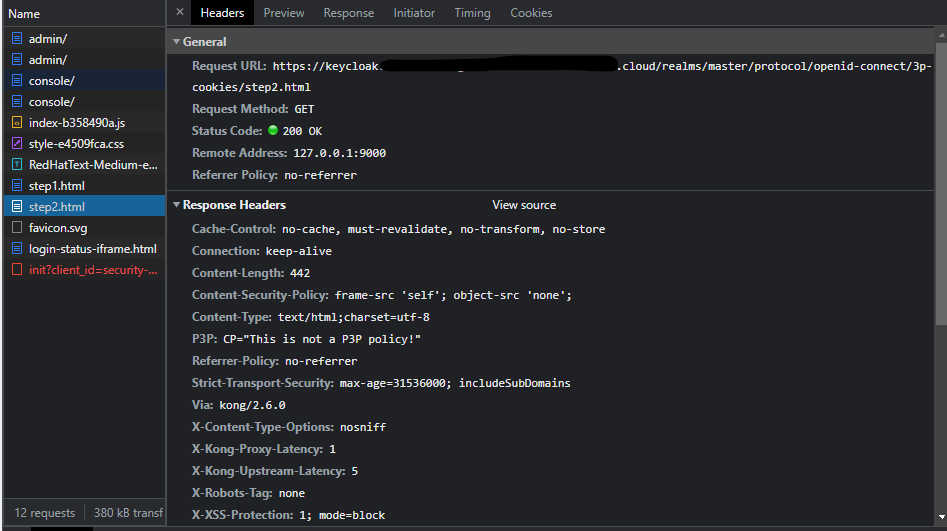
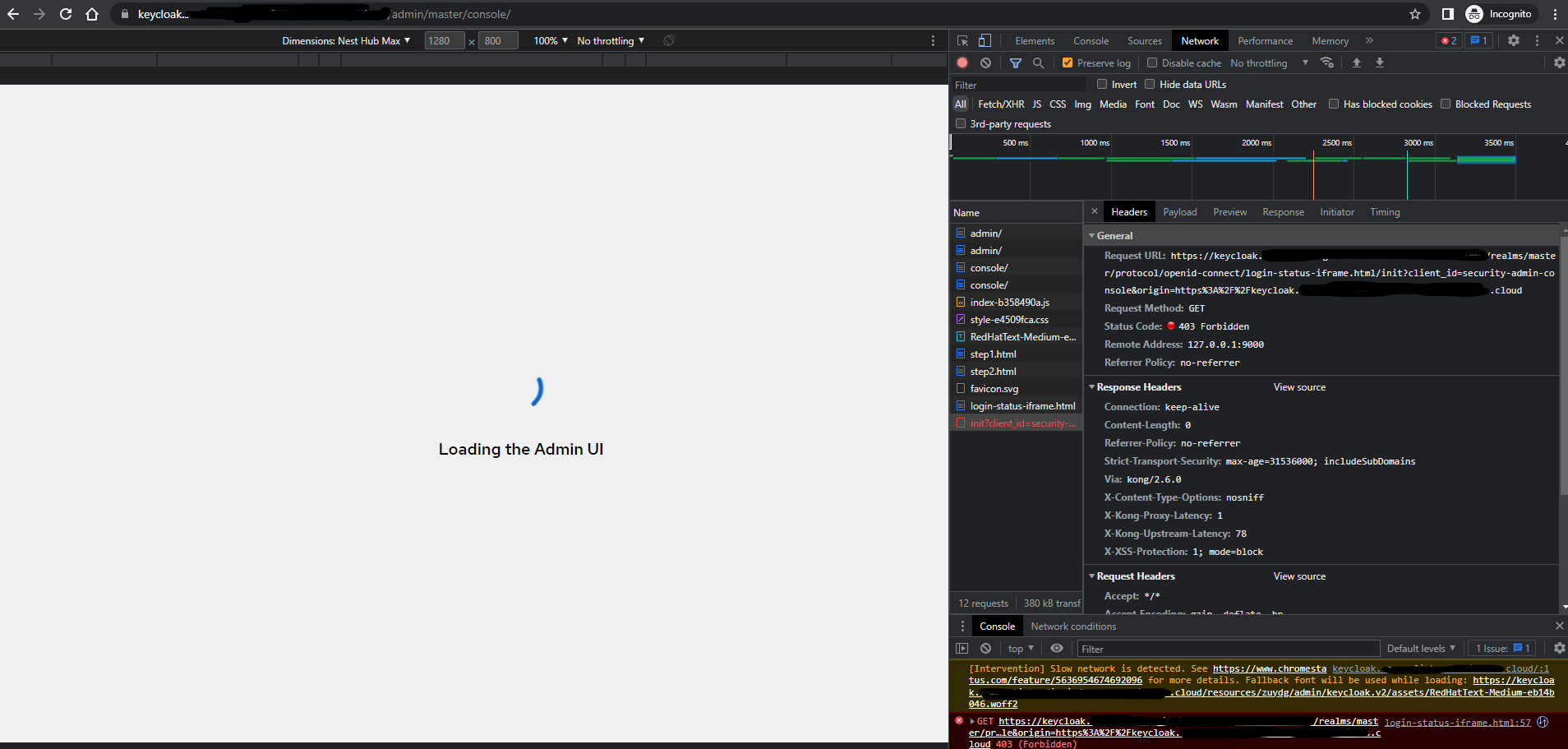
here is my kc.yaml
here is my ingress.yaml
can any one help me here.
Proxy edge doesn’t fix access to the admin console when you are behind a proxy and not using the default port. Our solution has been to manually specify the X-Forwared-Port to the externally used port rather than the internal port which normally gets forwarded. The admin console seems to use that port properly (where it ignore the hostname-port property).
In my case it wasn’t working, because I specified the
hostname-port=443, but should have removed it at all.In my setup, both Keycloak frontend and admin UI were behind a proxy (
proxy=edge) and were both exposed under default port 443 (although they had different hostnames though this is irrelevant).Keycloak’s frontend was configured to build URLs from incoming request, but they all had port 443 in them because of the
hostname-port=443. Admin URL was configured viahostname-admin-urland didn’t have port in it. As I found out thehostname-admin-urlwas not used at all in admin UI.Keycloak admin UI relies on the following code:
resources/libs/keycloak-js/dist/keycloak.mjs
Because 443 is a default for HTTPS browser was ignoring it, and
event.originvalue was simplyhttps://keyloak.example.com.Value of
loginIframe.iframeOriginon the other hand was set from OpenID Configuration, and those URLs contained port 443, so the aboveifwas evaluated tofalse, because:So nothing was happening.
As I already mentioned, OpenID Configuration was enforcing the port in URL because
hostname-portwas explicitly set to 443, removing this value (defaulting to -1), removed the port from URLs and things started working again.I would expect that Keycloak could be a bit smarter here, even if it just means fixing the URL comparison, as these are effectively the same:
https://example.com == https://example.com:443But also it could omit port from OpenID Configuration if it matches default ports (80 for HTTP, and 443 for HTTPS).
Hope this helps somebody.
For people using load balancer -> nginx ingress controller, these configs worked for me without using dev mode, no other http or hostname environment variables were used.
Without /auth
With /auth
For deployment via Helm, from https://artifacthub.io/packages/helm/bitnami/keycloak/ , I had to add this to
values.yml:to avoid this issue.
Thank you so, so much!
In my case, I had configured everything explicitly in the Apache Webserver proxy configuration and in keycloak.conf. The latter had
and the admin page was not working (only showed the loading message). The welcome page was working, though.
After removing the ports in the URLs, everything works!
After hours of trying and reading I got it working with this configuration:
Important to state here is: I removed the port from the URLs and set strict-ssl to true. Prior to this changes it wasn’t working, loading wheel was spinning endlessly.
I’m using the latest 22.0 behind an apache proxy and didn’t set
PROXY_ADDRESS_FORWARDING=true!Hope that helps.
I’m using Keycloak 22.0.5, in order to avoid having to change the endpoints of all the microservices I have to reuse the path “/auth”, to keep it works like this:
I am not able to load the admin console when I specify the port, this is behind a nginx proxy. The admin page just spins foreever. When I don’t specify the port everything works perfectly, even though I am specifying the same port that I am using by defaul. Here is the debug hostname output. I realize I can just not specify the port at all for this case, but I am trying to run on a non-default port, like 444, which also doesn’t work, although in that case it does report that the admin console has failed on the debug page.
It seems like I need to get the port into the admin console route but I’m not sure how. I need to be able to access the page from different sites so I can’t hardcode the full admin url and port which does work.
With the configuration the admin page spins forever, no error reported.
Admin page also spins in this configuration, Chrome does report a 403 error as well.
A stupid Idea later and I could fix it myself 😃 Problem was that the user I created couldnt read the files and I tried it with root and it worked without any problems.
Yes, the following is set in our keycloak yaml
Like I mentioned, it works in Chrome for some reason. 😃
This worked for me using ArgoCD:
I am having the same issue with 21.0.2. The provided workaround is not working.
well, I just solved the issue by using the browser debug console and solve each error one by one, here are some VERY important things I learned in the process. This is my setup: frp tunnel as the TLS terminator -> traefik -> keycloak, all inside the same podman pod, so the ports I exposed to the host system is irrelevant, all traffic is passing through the frp tunnel. following the server guides, I have my keycloak.conf file like this:
I’ll explain each relevant settings:
https://mydomain.com:myport/realms/master/protocol/openid-connect/login-status-iframe.html/init?client_id=security-admin-console&origin=https://mydomain.com:myport. This mismatch result in a 403 forbidden error when requesting the login endpoint. You’ll have to manually set hostname-admin-url’s scheme to https to make the system allow https origin.The only time (and even then it is questionable) to use HTTP in production is when TLS is terminated in a proxy. It does not make sense to expose Keycloak over HTTP even to internal clients. That is a risky an inherently dangerous thing to do. Bear in mind that you are sending credentials and tokens in clear text between Keycloak an internal clients in these cases, and don’t believe your firewall will always protect you.
You can always only have a single frontend URL, and a single admin URL, for Keycloak. It is not possible to expose Keycloak over multiple URLs (external/internal) with the built-in hostname provider. If you need to be able to do this you need to either disable the hostname provider, and enforce host headers, etc. at the proxy level (ideally also for internal clients), or you can implement a custom hostname provider.
Hi!
I noticed that the official command to run a development Keycloak instance as a docker container also leads to an unreachable admin console.
http://localhost:8080/adminshows aHTTPS requirederror message.Hello, I have the same issue.
Note that my keycloak is the latest version (19.0.3).
My admin console is stuck at loading. My keycloak conf file is:
hostname_url=http://hostname_test.com:8080but the admin console is stuck as well.Am I making any mistakes in my configuration?