hvac: Missing client token with approle
Hi,
Vault 0.11.3 and hvac 0.6.4.
Probably not an issue, but this “used to work before” (like Vault 0.10 and hvac 5.x).
Reproducing the following flow:
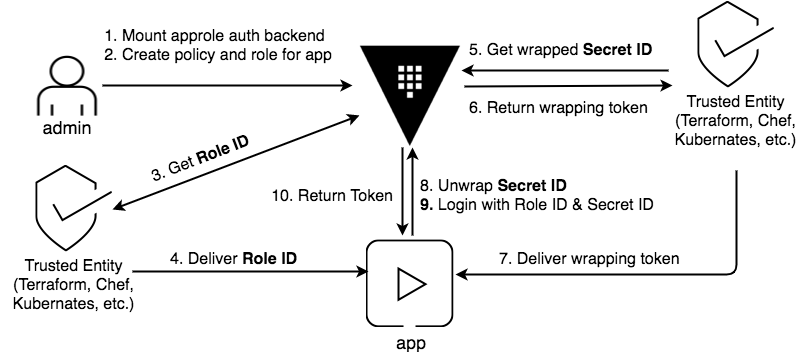
Piece of the code failing:
def get_vault_token(vault_rolename):
# get role id from vault-tower
role_id_json = requests_wrap.get_data("{}{}/{}".format(vault_token_tower, "/roleid", vault_rolename))
role_id = role_id_json['role_id']
print("roleid: {}".format(role_id))
# get secret wrap from vault-tower
wrapped_token_json = requests_wrap.post_data("{}{}/{}".format(vault_token_tower, "/wraptoken", vault_rolename))
wrapped_token = wrapped_token_json['wrap_token']
print("wrapped token: {}".format(wrapped_token))
# unwrap token to get secretid
# Failing here
unwrapped_secret_id = vc.unwrap(wrapped_token)
print(unwrapped_secret_id['data']['secret_id'])
print("Secret id: {}".format(unwrapped_secret_id))
with the following – see https://gist.github.com/madchap/f7efd023c9c6f6058c4b8192aa97323c
The policy associated with the role is the following:
# Login with AppRole
path "auth/approle/login" {
capabilities = [ "create", "read" ]
}
path "auth/approle/role/torrent9scraper" {
capabilities = [ "create", "update", "read" ]
}
Basically, any action with object vc fails with that error (i.e- vc.set_role_id(), or vc.create_token()) The vc Client only has the url param passed to it, no token obviously. I am using a simulated “trusted entity” to map to the schema.
With my “admin” profile from the CLI, I am able to unwrap with no problem.
I am a bit at a loss here. I definitely used to be able to unwrap a token this way before.
Thanks for shedding some light. Cheers, fred
About this issue
- Original URL
- State: closed
- Created 6 years ago
- Reactions: 2
- Comments: 16 (4 by maintainers)
I think providing an API similar to how the Vault CLI works would probably be the most useful for people. Perhaps following how the Requests library provides responses as an object with response.code for the status code, response.json for the json return, and response.text to dump it in a slightly nicer format for direct printing. Maybe
hvaccould wrap responses as a Python OrderedDict by default (simple_salesforce does this against the Salesforce API) and then offer an option to just get the raw JSON as mentioned above.Thanks for the input @reiven! FWIW, along those lines, the follow code snippet is what I’ve personally ended up with in a Django app hosted via Heroku that receives a wrapped secret_id and then instantiates a hvac client using those credentials (this may not be directly related to the most recent comments on this issue, but I figured it would be worth chiming in with my own usage in case its helpful for any other folks while we pin down what problem(s) this issue should be solving for):
[I haven’t actually exercised this code in some time, so I’ll try to loop back on that front and verify if its still relevant for the issue at hand at some point…]
I may have gotten slightly farther by putting
token=''into the initial constructor, now I’m fighting the AppRole policies which may not have gotten created properly. I’ll see if I can set up my own dummy instance of Vault with AppRoles/Namespaces and see how hvac handles the mix. I noticed looking at the code that “use_token=True” was scattered through a lot of methods, it seems like it might be useful to create an exception for “InvalidMissingVaultToken” and simply have any methods that need an actual token to raise the exception if it wasn’t defined viaauth_approleor passed in through the environment.