core: Pushover integration broken in 0.106.0
The problem
-
In addition to issue #32227 there are other parameter that are not working anymore. Using the
retryandexpire/priority: 2parameters results in a error400: retry is invalid -
Also @balloob the changes #31647 are breaking changes, which are not stated as such in the change log! At the moment there is no way to whitelist a URL only directories and there is no way to use a camera entity as data provider for the attachment part. Every other notification integration (with attachments) supports attachments via URL or path and suddenly there is a “small-pr” which breaks the pushover integration. However I do get the intended security thought behind this change, but you have to come up with a better plan than ban the attachment download via URL, either by whitelist URLs (with wildcards) or by a global setting which allows URLs.
-
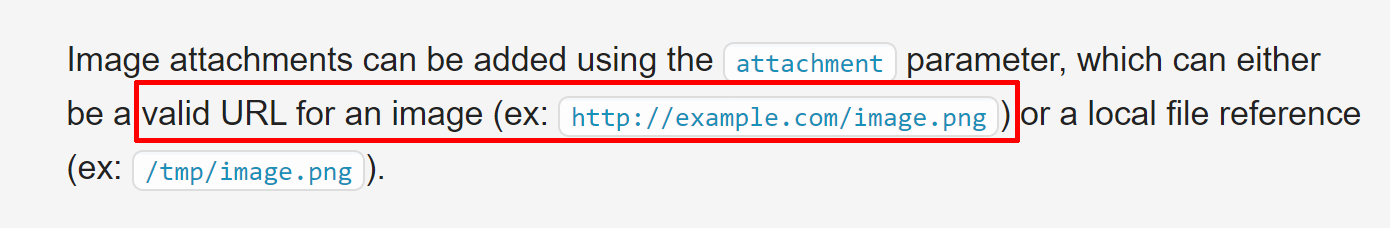
The docs are also not up to date
Environment
- Home Assistant release with the issue: 0.106.0
- Last working Home Assistant release (if known): 0.105.4
- Operating environment (Hass.io/Docker/Windows/etc.): Hass.io (Synology Package)
- Integration causing this issue: pushover
- Link to integration documentation on our website: https://www.home-assistant.io/integrations/pushover/
Problem-relevant configuration.yaml
notify:
- platform: pushover
name: pushover
api_key: !secret pushover_api_key
user_key: !secret pushover_user_key
notify.pushover
data:
attachment: 'http://admin:admin@192.168.1.1/blabla/picture'
expire: 300
priority: 2
retry: 30
sound: siren
url: 'homeassistant://'
url_title: Home Assistant
message: "Alert"
title: "Intruder"
Traceback/Error logs
Protokolldetails ( ERROR )
Logger: homeassistant.components.websocket_api.http.connection.139810526262928
Integration: websocket_api (documentation, issues)
First occured: 23:33:41 (1 occurences)
Last logged: 23:33:41
400: retry is invalid
Traceback (most recent call last):
File "/usr/src/homeassistant/homeassistant/components/websocket_api/commands.py", line 134, in handle_call_service
connection.context(msg),
File "/usr/src/homeassistant/homeassistant/core.py", line 1230, in async_call
await asyncio.shield(self._execute_service(handler, service_call))
File "/usr/src/homeassistant/homeassistant/core.py", line 1253, in _execute_service
await handler.func(service_call)
File "/usr/src/homeassistant/homeassistant/components/notify/__init__.py", line 119, in async_notify_message
await notify_service.async_send_message(**kwargs)
File "/usr/src/homeassistant/homeassistant/components/notify/__init__.py", line 185, in async_send_message
await self.hass.async_add_job(partial(self.send_message, message, **kwargs))
File "/usr/local/lib/python3.7/concurrent/futures/thread.py", line 57, in run
result = self.fn(*self.args, **self.kwargs)
File "/usr/src/homeassistant/homeassistant/components/pushover/notify.py", line 111, in send_message
html,
File "/usr/local/lib/python3.7/site-packages/pushover_complete/pushover_api.py", line 199, in send_message
callback_url, timestamp, sound, html)
File "/usr/local/lib/python3.7/site-packages/pushover_complete/pushover_api.py", line 160, in _send_message
return self._generic_post('messages.json', payload=payload, session=session)
File "/usr/local/lib/python3.7/site-packages/pushover_complete/pushover_api.py", line 88, in _generic_post
raise BadAPIRequestError('{}: {}'.format(resp.status_code, ': '.join(resp_body.get('errors'))))
pushover_complete.error.BadAPIRequestError: 400: retry is invalid
About this issue
- Original URL
- State: closed
- Created 4 years ago
- Reactions: 6
- Comments: 23 (4 by maintainers)
Exactly this. Your server has access to servers that are not externally accessible. Now by allowing anyone to just send in a URL, Home Assistant will fetch this for you and send it to anyone in the world. If someone gets an access token for a user account (including non admin), they can now send any internal content out. When that happens, the news won’t mention that @peetipablo’s server gets hacked. Nope, they will write that Home Assistant got hacked.
So yeah, we took this feature out and it won’t come back. If you feel like you have an acceptable solution that you’re also willing to implement, feel free to open an architecture issue with your proposal and let’s discuss!
That would be the hack right there though? If someone’s got an access token, there’s plenty enough damage they can do.
I was using URLs for Pushover notifications from my Zoneminder cameras, and this change broke it. I’m now using the downloader component to grab the URL to a file first and then send it, so effectively by enabling downloader I have exactly the same vulnerability - someone with a token could do the same thing. It’s no more secure, but it was less convenient to set up.
Incidentally, I can’t use the camera snapshot to grab the file, because I want to use Zoneminder’s ability to grab the frame ID that caused the alarm.
If the concern is admin vs. non-admin rights if a token is stolen, then do non-admin users even have the ability to call services directly? If they do, perhaps they shouldn’t?
FYI… If you’re doing this as part of a script or automation, as a workaround you can just save the camera snapshot locally to use as a file with Pushover. Something like…
I’d definitely like URL support back though. 😃
I lost hours today trying to figure out why the URL attachment was not working, until I saw this PR and see the documentation is not in-line with the code 😦
In that case this change should have been marked as breaking change and the documentation should have been purged of all references to attaching URLs for all notification integrations.