core: 2FA broken with Synology DSM version 7.0.1-42218 update 2
Checklist
- I have updated to the latest available Home Assistant version.
- I have cleared the cache of my browser.
- I have tried a different browser to see if it is related to my browser.
Describe the issue you are experiencing
Since restarting HA this morning, I have a notification that let’s me know that I need to reconfigure my Synology integration. I follow the steps and use my login/password + 2FA and get success message. However, the integration does not update and show connection. I’ve restarted several times and it’s still showing the same problem.
Describe the behavior you expected
I expect after successfully logging in that it works and the integration refreshes properly.
Steps to reproduce the issue
1.Click Reconfigure button in integration page for Synology 2.Login in with username, password, and then 2FA code
…
What version of Home Assistant Core has the issue?
core-2021.12.10
What was the last working version of Home Assistant Core?
core-2021.12.10
In which browser are you experiencing the issue with?
Google Chrome Version 97.0.4692.99 (Official Build) (x86_64)
Which operating system are you using to run this browser?
macOS Big Sur 11.6.2
State of relevant entities
No response
Problem-relevant frontend configuration
No response
Javascript errors shown in your browser console/inspector
Logger: homeassistant.config_entries
Source: config_entries.py:327
First occurred: 1:23:40 PM (1 occurrences)
Last logged: 1:23:40 PM
Config entry '192.168.[xxx.xxx]' for synology_dsm integration could not authenticate: reason: Two-step authentication required for account: [myaccountusername]
Additional information
No response
About this issue
- Original URL
- State: closed
- Created 2 years ago
- Reactions: 26
- Comments: 90 (31 by maintainers)
There is nothing we can do from HA side, since it is a bug in the API of DSM version “7.0.1-42218 update 2”. Unfortunately there is no (visible) progress in the Synology support ticket, yet (see https://github.com/home-assistant/core/issues/64867#issuecomment-1024963725)
But feel free to open an support ticket on your own with Synology and reference to #3011170 - feel free to use the following as template/blueprint:
Further I would kindly ask you to ❗ stop commenting, that you have the same issue, unless have any further helpful information to solve the issue ❗ please use just the 👍 button on the initial post. This will help to keep the overview in this issue, thx.
I have filed a support ticket with Synology, but cannot promis, that they will fix this … further I cannot really do any additional debugging or other checks, which could be requested by Synology within this support ticket, since my NAS is still on the unaffected version.
so cross fingers 🤞
@littletruckman nice finding 👍 so this is definitely a bug in DSM, since it worked well with
format=sid(it is also like documented) before “DSM 7.0.1-42218 Update 2” Will cross-chek this later this week and do a proper update of the underlying libraryI did and I got the information that they forwarded things to their development team, but can’t give any time frame on when the issue will be fixed. The last update to the ticket was two days ago. If it had been fixed in the beta, the would likely have directed me to download that.
Hi,
2FA in Home Assistant integration stopped working for me after upgrading to DSM 7.0.1-42218 Update 3. On update 2 it worked fine for me. I run HA on a HA Blue, so it is not running on the Synology in Docker or VM.
Thanks again for the solution. It works like a charm!
As agreed, an update from the support from Synology for those who are interested.
After trying to discuss about: should we use “version=7” or “version=6” they finally agreed that “version=7” is OK (it is given has “maxVersion” in the SYNO.API.info answer.
They also recognized that the issue is due to the tag “format=sid” and this is now an identified problem that will be solved in a future DSM Update…
Best regards and thanks
I would not hold my breath. Their last responses to my ticket came close to satire (they told me to subscribe to their newsletter for any “news and changes” resulting from my ticket 🤡).
On the release notes of DSM 7.1-beta I can not see a proper fixed mentioned
Edit: tested 7.1 beta with a vDSM, unfortunately the issue still persists
And mine: #3043290 BR
@mib1185 I have placed the findings in the ticket I had by the Synology support. I hope it will help to have a move from their side or at least a recognition of the bug/regression. I’ll keep you informed.
Thanks @mib1185
Here are the results:
&format=sidbash-5.1# curl -vvk https://DS918-IP:port/webapi/entry.cgi?'account=SynoUser&passwd=SynoPassword&enable_device_token=yes&device_name=homeassistant&format=sid&otp_code=908666&api=SYNO.API.Auth&version=7&method=login'=> “device_id”:“”
&format=sidbash-5.1# curl -vvk https://DS918-IP:port/webapi/entry.cgi?'account=SynoUser&passwd=SynoPassword&enable_device_token=yes&device_name=homeassistant&otp_code=270498&api=SYNO.API.Auth&version=7&method=login'=> “device_id” is now set ! As well as
didcookie…Default behavior of the SYNO.API is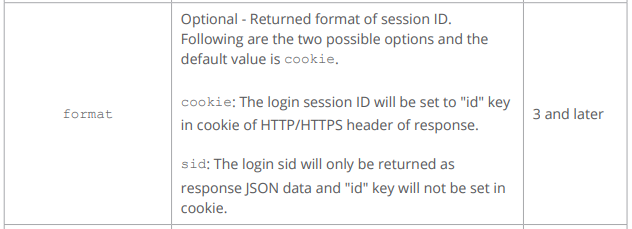
That’s why I had Postman working because my PC was previously connected to DSM Manager and had a “did” cookie that identify the device for SYNO.API…
What do you think about trying to remove the
&format=sidin the logon query(ies) ?@mib1185,
Found some time to do it once 😃
Attached you will find the complete log:
BR
home-assistant - LittleTruckMan.zip
@mundschenk-at this is exact the issue, we are trying to catch here 👍
let me try to summarize the available data
@littletruckman from https://github.com/home-assistant/core/issues/64867#issuecomment-1070888018
GET https://my.syno.ip.adresse:sslport/webapi/entry.cgi?api=SYNO.API.Auth&version=7&method=login&account=<user>&passwd=<password>&otp_code=123456&enable_device_token=yes&device_name=postman&format=sid@mundschenk-at from https://github.com/home-assistant/core/issues/64867#issuecomment-1071168707
GET https://<IP:port>/webapi/entry.cgi?api=SYNO.API.Auth&version=7&method=login&account=<user>&passwd=<password>&otp_code=<code>&enable_device_token=yes&device_name=postman&format=sid@j6s33m extracted from debug.txt from https://github.com/home-assistant/core/issues/64867#issuecomment-1021638882
https://[mysynologyIPaddress]/webapi/entry.cgi?account=********&passwd=********&enable_device_token=yes&device_name=[mySynologyNASname]&format=sid&otp_code=077221&api=SYNO.API.Auth&version=7&method=loginbased on the summarization @littletruckman may I ask you, to please verify again your results?
When I run
GET https://<IP:port>/webapi/entry.cgi?api=SYNO.API.Auth&version=7&method=login&account=<user>&passwd=<password>&otp_code=<code>&enable_device_token=yes&device_name=postman&format=sid, I get the following result:I am assuming
device_idshould contain a value? It does not for me.Hello, I am not a developer but a regular user of Synology and Home Assistant. Since I am experiencing the issue, I tried to help and posted a ticket to Synology Support yesterday and got an answer today. They were asking me to share with them the API script and the results.
So I did my first steps in postman and find out that the 3 steps are working correctly and that, at the opposite of what is described in the “step to reproduce” (https://github.com/home-assistant/core/issues/64867#issuecomment-1042862897) the “did” parameter is back, returned by the API 😦
So what can I answer to Synology Support to keep their focus 😃 ?
BR
Postman results:
You will nozice that the “did” parameter is returned
Seems DSM 7.0.1 Update 3 was released and Update 2 was pulled, from the release notes it doesn’t look like the bug is solved
FYI: https://www.synology.com/en-global/releaseNote/DSM#7_0
Yes I’ve done the above and 2FA works as it’s supposed to. It’s the HA integration that is broken.
From: Michael @.> Sent: Tuesday, January 25, 2022 5:10:40 PM To: home-assistant/core @.> Cc: Jordan @.>; Mention @.> Subject: Re: [home-assistant/core] Synology 2FA Broken Again (Issue #64867)
Could you please do a further test?
The OTA code should not be asked while re-login, since “remember this device” was enabled.
Will you log the bug w/ Synology?
I’m not familiar with the support contact possibilities for developer (API) related issues 🤔 Maybe I find some spare time on upcoming weekend, but cannot promise that.
— Reply to this email directly, view it on GitHubhttps://github.com/home-assistant/core/issues/64867#issuecomment-1021694457, or unsubscribehttps://github.com/notifications/unsubscribe-auth/AEIZISXBP75QKYF7RQ6JRVTUX4UXBANCNFSM5MWLBCLQ. You are receiving this because you were mentioned.Message ID: @.***>
Sorry, forgot to mention that - just save the logs in a txt file and drag&drop it here - so it will be added as attachment
I removed some of my information (url, NAS name, token, etc)