terraform-provider-google: google_cloud_run_service can't be initially created with secret manager env vars
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request.
- Please do not leave +1 or me too comments, they generate extra noise for issue followers and do not help prioritize the request.
- If you are interested in working on this issue or have submitted a pull request, please leave a comment.
- If an issue is assigned to the
modular-magicianuser, it is either in the process of being autogenerated, or is planned to be autogenerated soon. If an issue is assigned to a user, that user is claiming responsibility for the issue. If an issue is assigned tohashibot, a community member has claimed the issue already.
Following the previously reported bug #9175 I have finally been able to isolate the problem. This will only fail if the cloud run service hasn’t been created before. The way to fix it is to manually enter a secret env var through the console and then applying again.
Terraform Version
Terraform v1.0.0
on linux_amd64
+ provider registry.terraform.io/hashicorp/google v3.72.0
+ provider registry.terraform.io/hashicorp/google-beta v3.72.0
+ provider registry.terraform.io/hashicorp/random v3.1.0
+ provider registry.terraform.io/newrelic/newrelic v2.23.0
Affected Resource(s)
- google_cloud_run_service
Terraform Configuration Files
locals {
env_secrets ={
SECRET_KEY : "projects/994503404540/secrets/api_secret_key"
}
project = {
id: "cybernetic-tide-317715",
region: "europe-west1"
}
}
resource "random_uuid" "secrets" {
for_each = local.env_secrets
}
locals {
# Secrets seem
secret_uuid = {for env_name, secret_id in local.env_secrets : env_name => "secret-${random_uuid.secrets[env_name].result}"}
secret_mappings = {for env_name, secret_id in local.env_secrets : env_name => "${local.secret_uuid[env_name]}:${secret_id}"}
run_googleapis_com_secrets = join(",", values(local.secret_mappings))
}
resource "google_cloud_run_service" "instance" {
provider = google-beta
project = local.project.id
name = "test"
location = local.project.region
autogenerate_revision_name = true
template {
metadata {
annotations = {
"run.googleapis.com/launch-stage" = "ALPHA"
"autoscaling.knative.dev/maxScale" = 1000
"run.googleapis.com/client-name" = "terraform"
"autoscaling.knative.dev/minScale" = 1
"run.googleapis.com/secrets" = local.run_googleapis_com_secrets
}
}
spec {
container_concurrency = 80
timeout_seconds = 299
containers {
image = "us-docker.pkg.dev/cloudrun/container/hello"
dynamic "env" {
for_each = local.secret_uuid
content {
name = env.key
value_from {
secret_key_ref {
name = env.value
key = "latest"
}
}
}
}
ports {
container_port = 8080
}
resources {
limits = {
"cpu" = "1"
"memory" = "1Gi"
}
requests = {}
}
}
}
}
}
terraform {
required_version = "= 1.0"
required_providers {
google = {
source = "hashicorp/google"
version = "= 3.72.0"
}
google-beta = {
source = "hashicorp/google-beta"
version = "= 3.72.0"
}
}
}
Debug Output
https://gist.github.com/txomon/818300abee68a210b08723e0dad6a584
Panic Output
Expected Behavior
Cloud run instance should have been created
Actual Behavior
It didn’t get created
Steps to Reproduce
- New cloud run instance. If it was previously created it will work
terraform initterraform apply
Important Factoids
This will ONLY fail if the cloud run instance doesn’t exist
References
Workaround
- Create the google_cloud_run_service without any secrets referenced (in the example
secret_envempty and"run.googleapis.com/secrets" = local.run_googleapis_com_secretscommented out - Go to the console, open the service, click on
Edit and deploy new revisionbutton - Go to the
Variables and secretstab, click on secrets, and add the resource by id by clicking on the lower buttonDON'T SEE YOUR SECRET? ENTER SECRET RESOURCE ID.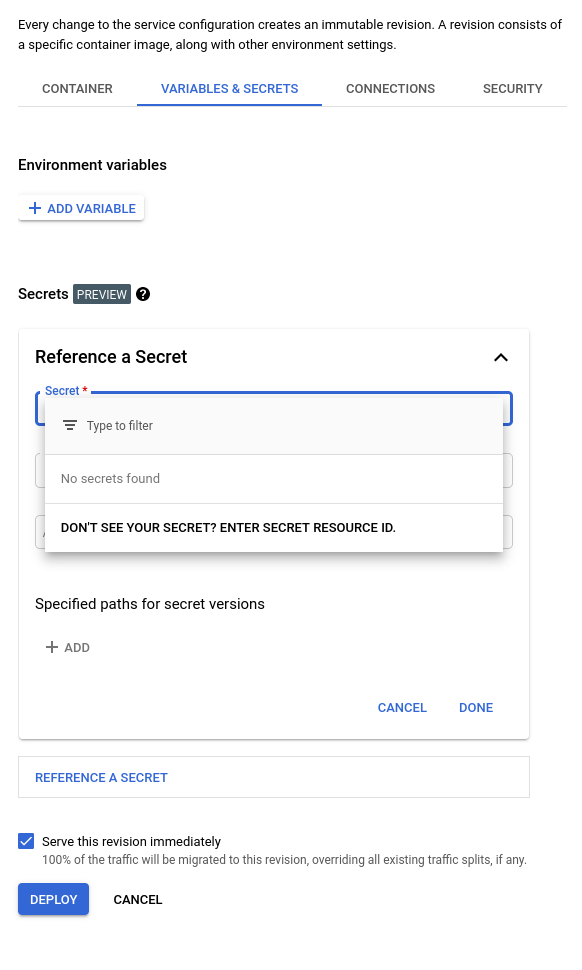
Reference Method -> Exposed as environment variable- Add the name and the version
- click
Done Deploy- Go back to your terraform files, and restore all the code commented in step 1, it should be able to apply now
About this issue
- Original URL
- State: closed
- Created 3 years ago
- Comments: 17
@edwardmedia it seems to work when setting it in the outer field. Thank you!
Which annotations should go in the outer
metadata.annotationsfield and which ones in the innertemplate.metadata.annotationsfield? The API documentation has both objects but it fails to mention any difference on the two fields and so far I had assumed they were interchangeable.@txomon can you try adding below
metadataat the root of the resource? Let me know if that works for you. Your UUID is fine