terraform-provider-azurerm: Service Bus Namespace Network Rule Set doesn't always set default_action to Deny when specified
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request
- Please do not leave “+1” or “me too” comments, they generate extra noise for issue followers and do not help prioritize the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Terraform (and AzureRM Provider) Version
Terraform: 0.14.6 AzureRM Provider: 2.83.0
Affected Resource(s)
azurerm_servicebus_namespace_network_rule_set
Terraform Configuration
resource "azurerm_resource_group" "example" {
name = "example-resources"
location = "CentralUS"
}
resource "azurerm_servicebus_namespace" "example" {
name = "example-sb-namespace"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
sku = "Premium"
capacity = 1
}
resource "azurerm_servicebus_namespace_network_rule_set" "example" {
namespace_name = azurerm_servicebus_namespace.example.name
resource_group_name = azurerm_resource_group.example.name
default_action = "Deny"
}
Expected Behaviour
azurerm_servicebus_namespace_network_rule_set sets default_action to “Deny”
Actual Behaviour
default_action does not get set to “Deny”. Subsequent applies will show as wanting to change from “Allow” -> “Deny”, but will not actually change the value.
Steps to Reproduce
terraform apply
Description
I’d like to use a Private Endpoint on the Service Bus Namespace and Deny all traffic by default via azurerm_servicebus_namespace_network_rule_set. However, if I don’t specify ip_rules or network_rules, it doesn’t set the default_action to “Deny”. If I specify ip_rules and/or network_rules it sets the default_action as intended.
About this issue
- Original URL
- State: closed
- Created 3 years ago
- Reactions: 4
- Comments: 21 (6 by maintainers)
No worries, yes, I think we need to expose the publicNetworkAccess in terraform as well, let me have an intertal discussion and get back to you guys.
Just in case you are interested what UI does when public access is disabled: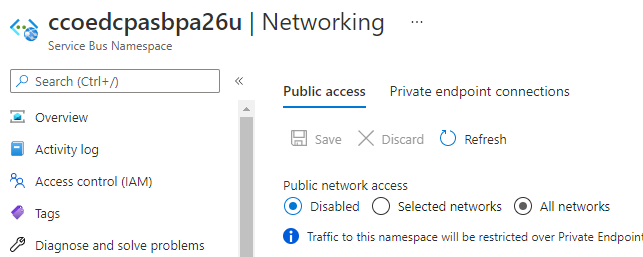 It sets default action to allow when publicNetworkAccess is Disabled.
It sets default action to allow when publicNetworkAccess is Disabled.
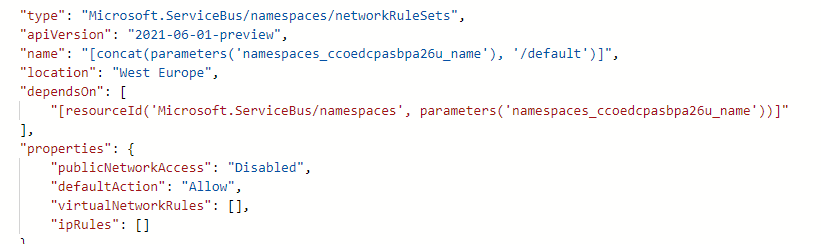
So a combination of default_action = allow and public_network_access_enabled = false will do the job finally.
Awesome, thank-you @xiaxyi! And Happy New Year! 🙃
in the azure portal, you can absolutely set the network to public access disabled, whch means default rule is to deny, with an empty IP filter and empty virtual network list. this means that only private endpoint addresses are allowed. The portal states “Traffic to this namespace will be restricted over Private Endpoints only.”
after disabling public access in the portal, tf is still reading the default action as “allow”. so maybe the question is where is this attribute being read from? its almost as if an empty ip filter is automatically read as “default_action = allow”. disabling public access and setting default action to deny do not appear to be the same thing.
the azure api mentions a publicNetworkAccess property. seems like this really needs to be exposed, and allow an empty ip filter with default action deny
@xiaxyi as posted above the explained behavior is not what we want. This is exactly opposite.
I also ready asked to explain what will
default_action = Allowwith empty ip_rules will do? Will it block everything or allow everything (because by sense Allow with empty array allows nothing)? if it’s not the case we MUST have a possibility to set Deny with empty ip_rules meaning everything is blocked.I can also reproduce using the latest AzureRM 2.84.0 and Terraform 1.0.10.
What’s more, it’s not a “it won’t change it”, but it WILL change it to the wrong value. For example, if I manually “fix” it in the Azure Portal (“Allow access from: Selected Networks”), then on the next
terraform apply, Terraform will:Allow(which is incorrect)AllowtoDenyAllowwhen applied (oops!)Thank-you, @wozneyr, for pointing out that it works when
ip_rulesit set. Setting it to an empty list ([]) didn’t work, but I set it to["127.0.0.1/32"]and that worked. It not only correctly setdefault_actionback toDeny, but the nextterraform planshowed everything matched the configuration. (I can use this at least as a temporary workaround until fixed)