gocd: Can't add user into a GoCD role behind CloudFlare minification proxy
Issue Type
- Bug Report
Summary
Environment
Basic environment details
- Go Version: 21.3.0
- JAVA Version: 15.0.2
- OS: Linux 5.4.129+
- Browser vendor and version (if relevant): Chrome 96.0.4664.93
Additional Environment Details
Steps to Reproduce
- MainNavigation:ADMIN->Roles configuration
- Add a new GoCD Role.
- Edit the role just created. Add a user and Save .
Expected Results
The user was added into the role.
Actual Results
An error showed up like:Someone has modified the configuration for role ‘XXX’. Please update your copy of the config with the changes and try again.
Possible Fix
sorry
Log snippets
sorry
Code snippets/Screenshots
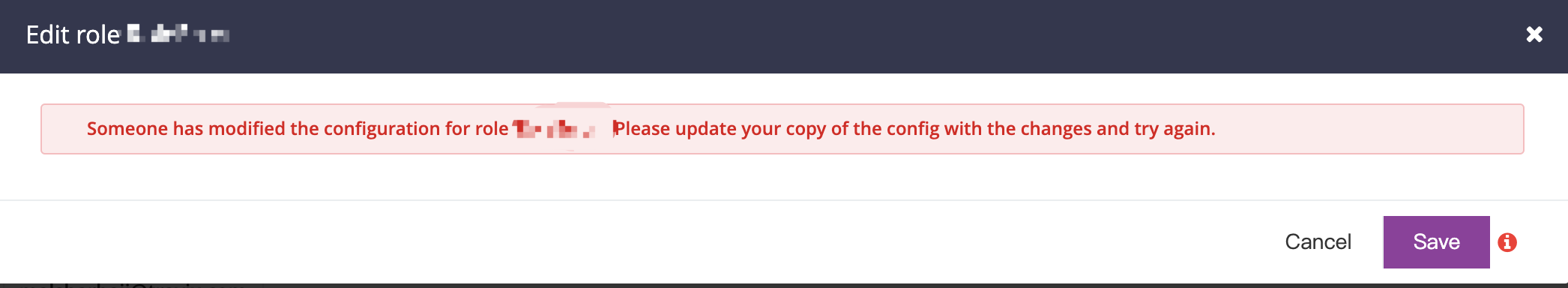
Any other info
sorry
About this issue
- Original URL
- State: closed
- Created 3 years ago
- Comments: 17 (9 by maintainers)
Indeed, we use cloudflare as a proxy. I created a Respect Strong ETags page role ,and it worked. Thanks again.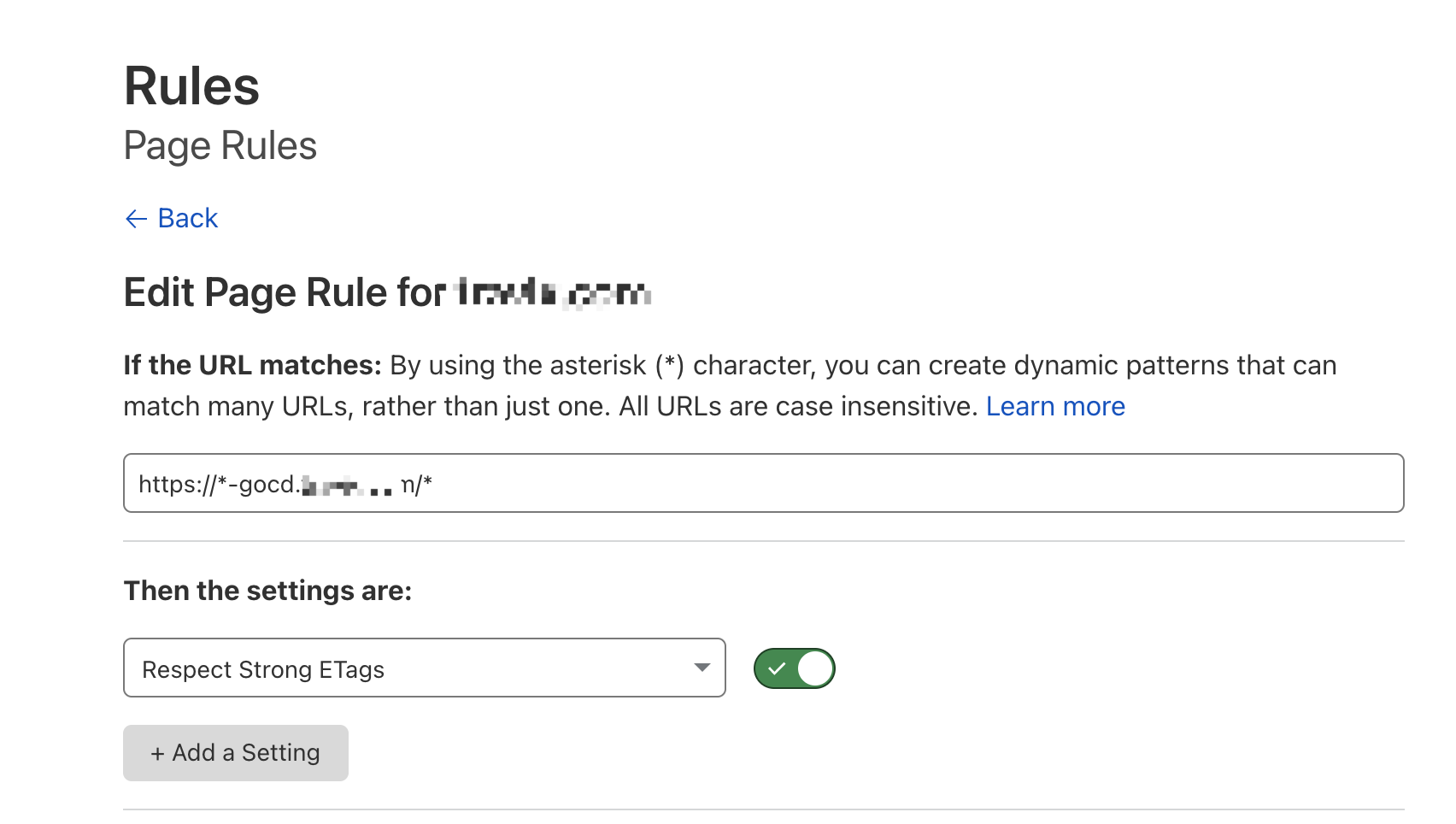
Thanks @arvindsv - I just came across that. I think the challenge here is that some proxies reserve the right to change the strong etags to weak (especially if they recompress responses), indeed that’s what Cloudflare’s documentation says they do without a page rule requiring enterprise plan, and is probably in line with the RFCs. However it says
The first two we should be doing sufficiently to stop it being the reason for conversion, but the 3rd point is out of our control and seems legit use of Cloudflare. My guess is Cloudflare minification is the main thing that might cause this (if it does so for JSON); I believe quite a lot of GoCD JSON is not pre-minified, so there is capacity for a proxy to minify and recompress.
Updating by Users Management probably works because these updates are a bulk
PATCHand there is no ETag or race-condition detection involved. I suspect this problem might occur on most of the CRUD APIs though, so it’s curious it’s been reported mainly against role edits and plugin settings (#9405), not other APIs.I am thinking that
If-Matchheaders if we are to continue with strong etags and strong etag validation on the backend, but need to think through the consequences of this.Cache-Control: no-transform, (see here) but need to be able to replicate somehow - and it seems to be legit for an intermediary to transform/minify/recompress anyway.Based on the
cf-rayresponse headers, looks like Cloudflare is there. I might need to re-read https://support.cloudflare.com/hc/en-us/articles/218505467-Using-ETag-Headers-with-Cloudflare and think about the consequences. Might need to change the logic inside GoCD to consider the weak etag == to a strong one for comparison purposes. Will need to think a bit more.