angular-auth-oidc-client: Tokens are missing after calling the refresh token
Hi!
I’m using v12.0.1 with Angular 12.1.1. I’d like to authenticate with code flow PKCE & refresh tokens. My config is as follows:
imports: [AuthModule.forRoot({
config:{
authority: 'http://127.0.0.1:8080/c2id',
redirectUrl: 'http://127.0.0.1:4200/login',
postLogoutRedirectUri: 'http://127.0.0.1:4200/login',
clientId: 'aowukh7pllgme',
scope: 'openid profile address email certificate',
responseType: 'code',
silentRenew: true,
useRefreshToken: true,
logLevel: LogLevel.Debug,
}
})
],
On the server side, the refresh token has no expiry and the accsess token lifetime is set to 30 sec. When that time is up, the new access token appears in the console, but after that, the refresh token no longer exists and the value of the access-, refresh- and id token are already null.
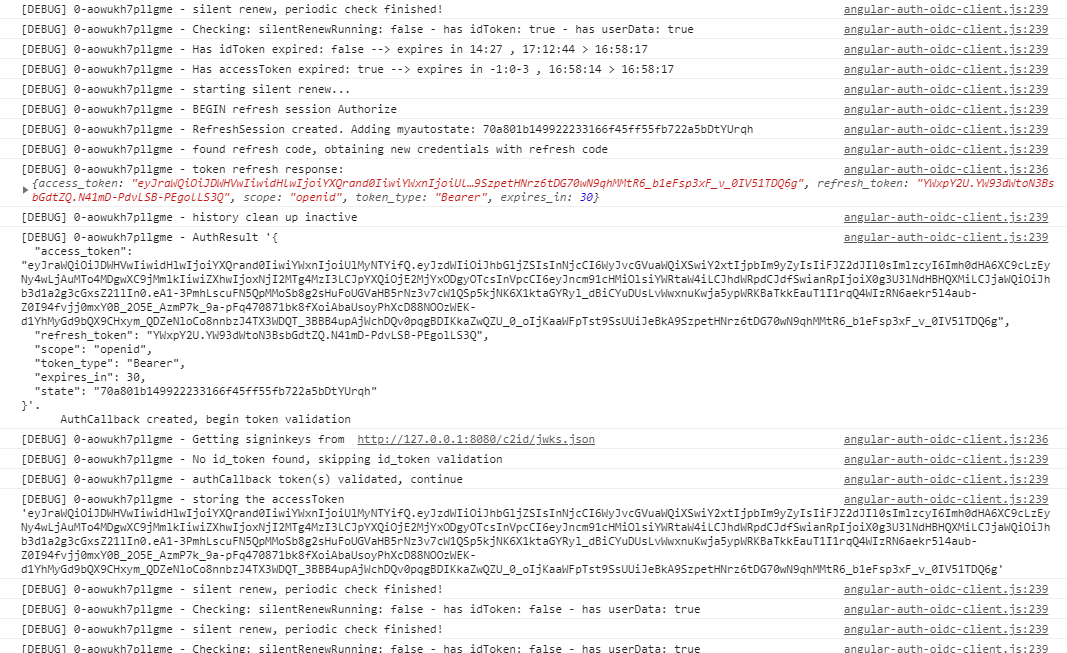
Maybe it’s a configuration failure, or something else?
Thanks!
About this issue
- Original URL
- State: closed
- Created 3 years ago
- Comments: 17 (4 by maintainers)
Refresh tokens should only be used in the browser if the extra mitigations required for refresh tokens are supported from the IDP. One time token usage, refresh token rotation are important, revocation as well. Refresh token without this might not be the best choice to secure your application if the IDP does not support this. Maybe if the IDPs cannot be updated for using refresh tokens in the browser, consider a server rendered application (BFF) or revert to iframes. None are perfect.
If the id_token is missing after a refresh, then I will add support for this, fix this. If the refresh token is not rotated, this cannot be fixed.
Greetings Damien
We have implemented refresh tokens so that the tokens can only be used once in browser as recommended for browsers. Using refresh tokens in the browser which can be used more than once is not recommended and not a good idea. If your IDP does not support refresh tokens one time usage, then you should not use refresh tokens in the browser. Consider changing your IDP or use a different authentication flow, renew.
Greetings Damien
Thank you!
I think the refresh token rotation supported from the IDP, because the c2id server config includes the following option to set this value:
In this case, the refresh token at the authorization and after 30 sec, is different.
However, after we got the second accsess/refresh token pair, the tokens already missing: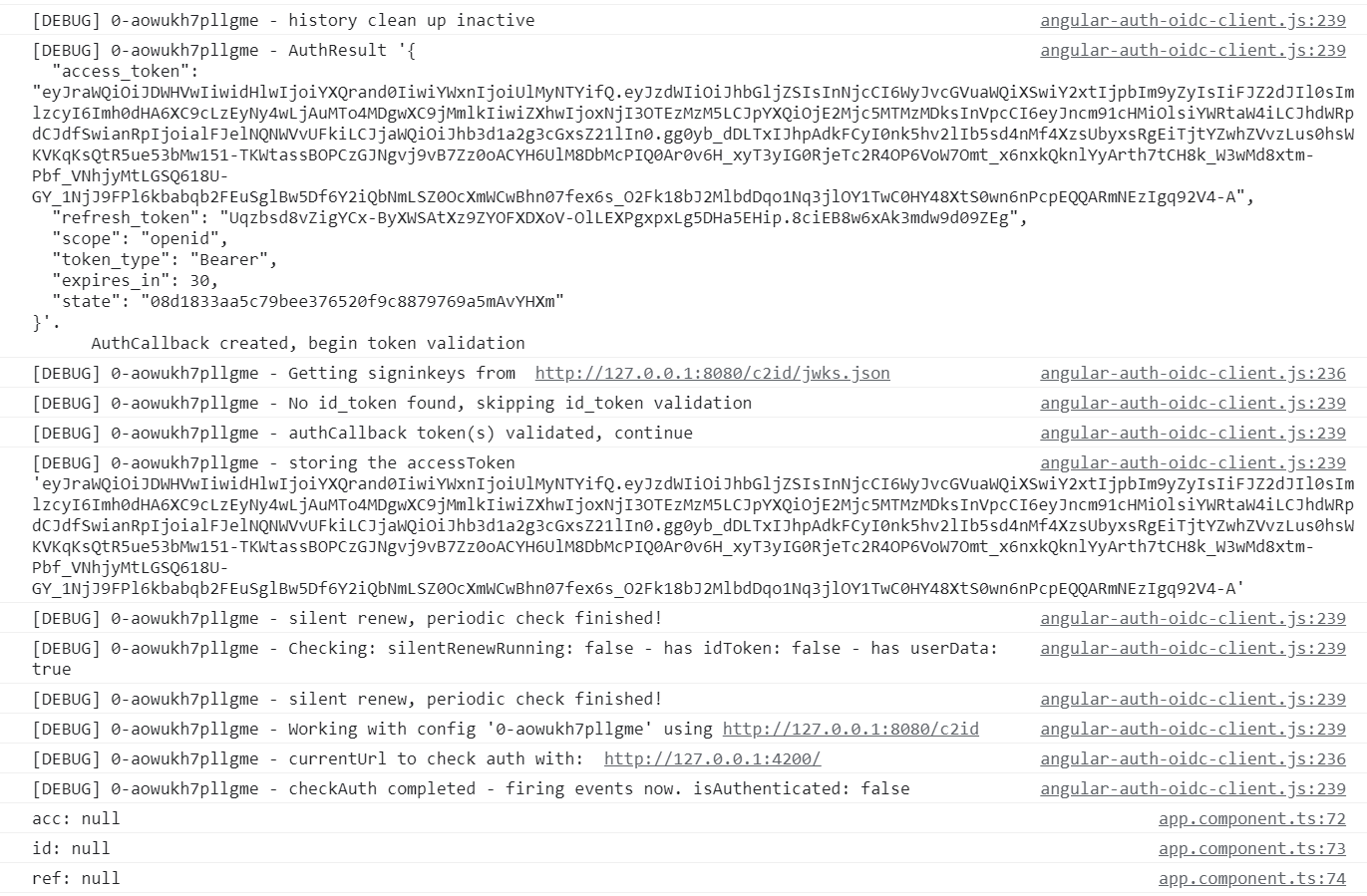
I have the same issue with cognito. on the first expiration I am able to get tokens just fine. But the one after that I have an error log saying “no refresh token found, please login”
Thank you for your answer!
I’m using the c2id as a sts server, but don’t found the opportunity to set the token rotation endpoint yet.