cluster-api-k3s: Control plane load balancer SSL health check fails
after applying the sample config
$ kubectl apply -f samples/aws/k3s-cluster.yaml
cluster-api-k3s successfully creates the vpc, control plane instance and load balancer.
However the load balancer doesn’t like how the apiserver on the control plane machine is talking https:
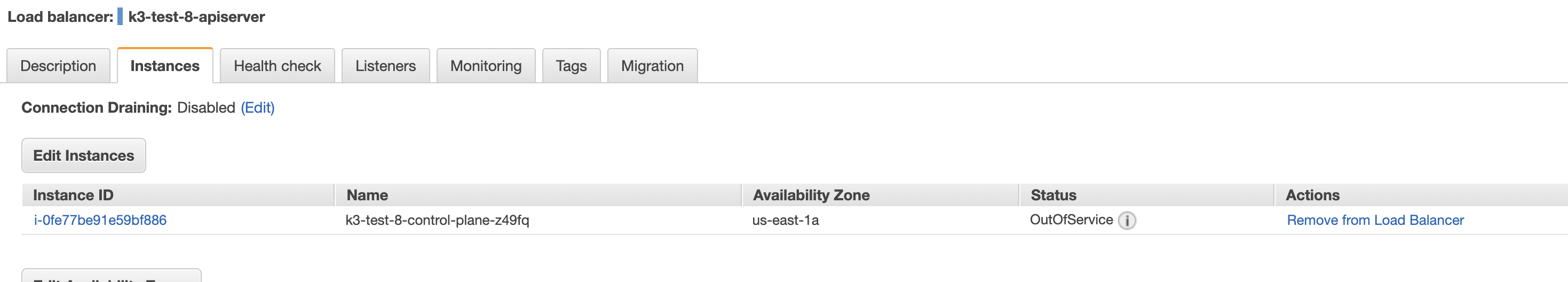
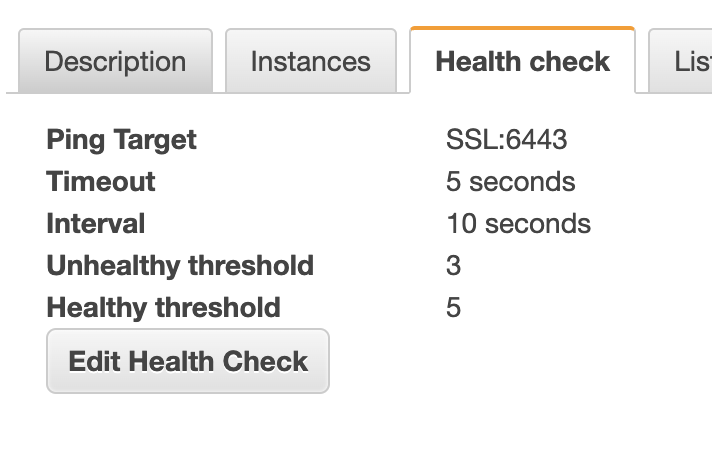
When I change the health check type to TCP it works just fine. The rest of the CAPI machinery successfully connects to the apiserver and proceeds with the bootstrap of the worker node just fine. The CA and the certificates appear to me to be correct.
About this issue
- Original URL
- State: closed
- Created 2 years ago
- Comments: 15 (13 by maintainers)
confirmed: no
I methodically compared the difference in behavior between a CAPA kubeadm based deployment and a cluster-api-k3s based one.
I ran a sample Go program with config generated by https://ssl-config.mozilla.org/#server=go&version=1.19&config=intermediate&hsts=false&guideline=5.6
which is the same config generator used by k8s itself, see https://github.com/k3s-io/k3s/blob/f8b661d590ecd1ed2ed04b3c51ff5e6d67cb092b/pkg/cli/server/server.go#L380
I shut down the api-server and ran it on port 6443, looking at the TLS handshakes performed by the AWS LB using tcpdump.
Let’s call
HostAthe host running kubeadm andHost3running k3s.The same program worked on HostA and didn’t work on Host3. The only difference were the TLS keypairs on the two machienes. I copied the keypair from HostA to Host3 and it worked on Host3 too.
tcpdump revealed that the negotiated cipher suite was
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)I modified the test program to include the ciphers included by default by k3s:
It didn’t work until I added
tls.TLS_RSA_WITH_AES_128_GCM_SHA256, which is similar to the includedtls.TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256but it doesn’t have the ECDHE prefix.This cipher is not chosen when I use the certificate created during k3s initialization. I conclude the certificate is not compatible with ECDHE.
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256means:I have layperson knowledge about how TLS works and I assumed that the DH exchange didn’t depend on the asymmetric crypto used to verify the certificate signature (here RSA I assume).
Yesterday I did quickly check the CA certificate and I found nothing unusual:
However, when looking at the actual certificate that used by the server (which is signed by the CA but is not the CA certificate), I can see it’s using elliptic curve crypto:
The file name is
/var/lib/rancher/k3s/server/tls/serving-kube-apiserver.crtand presumably created either by the k3s installer or by the k3s binary itself on first run.This to investigate:
Public Key Algorithm: rsaEncryptionTLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256?another example;
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256is supported by k3s, and we can use it locally with:but it fails with:
I find the TLS cipher/version matrix very hard to keep up with; I’ll try to figure out which ciphers need to be enabled so that it k3s works with TLS1.2