amplify-js: Unauthenticated access is not supported for this identity pool
Hi all 👋
I’m authenticating the user with
await Auth.signIn(emailOrPhone, password);
which completes finely. But when I try to get the credentials with
const credentials = await Auth.currentCredentials();
I get this error: Unauthenticated access is not supported for this identity pool
I’m setting up Amplify in this way:
Amplify.configure({
Auth: {
identityPoolId: 'xxx,
region: 'xxx',
userPoolId: 'xxx',
userPoolWebClientId: 'xxx',
},
});
(with actual values instead of xxx)
How do I authenticate in the Identity Pool and get temporary IAM credentials to use with the AWS SDK?
About this issue
- Original URL
- State: closed
- Created 6 years ago
- Comments: 24 (1 by maintainers)
Checking enable access to unauthenticated identites in cognito federated identities worked for me.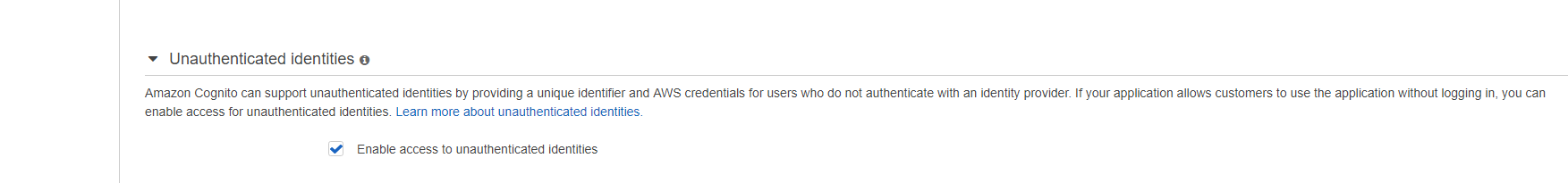
I have the same problem and this is not very helpful because with unauthenticated access it is functioning OK. I need to get it functioning with authenticated access.
So it’s just not me, Looks like the whole world is facing this issue.
For me the issue was a mismatch between the App Client ID and the associated Identity Pool. I fixed it by going to the Identity Pool in question, clicking Edit Identity Pool, expanding Authentication Providers, selecting the first tab (Cognito), and ensuring both the User Pool ID and App client ID were those that appear in my aws_config file.
I have the same issue where Auth.currentAuthenticatedUser() gives a successful user login, but subsequent
currentCredentialscall fails saying it’s trying to log the user in as an unauthenticated role.Fixed it. Had to enter exact information in the aws-amplify-config. In my case, just this & nothing else.
const amplifyConfig = { Auth: {
} };
@EgidioCaprino does your federated identity pool which has your user pool attached as an identity provider have an unauthenticated role attached to it? See here for detas: https://docs.aws.amazon.com/cognito/latest/developerguide/identity-pools.html
In the federated identities console, go-to your identity pool, edit, then make sure you have unauthenticated role enabled. Then make sure the role has a policy that allows what you would like to be done unauthenticated. Generally this is something like mobileanalytics-put and/or execute-api etc.
For anyone still facing the issue, you need to check if user received from Auth.signIn(email, password) has a challengeName: ‘NEW_PASSWORD_REQUIRED’ which is likely from creating a user in the console. If this is on the user, they need to enter a new password to be “authenticated”.
In order to do this, simply get the user (
const user = await Auth.signIn(...)) and the user’s input for the new password and run this just like a sign in:await Auth.completeNewPassword(user, newPassword). This will return an “authenticated” user (as far as passwords go).I got the error after updating the api from: being restricted to authenticated users only, to: allow unauthenticated users. Under
amplify/backend/auth/cognito[nnn]/parameters.jsonI switched:"allowUnauthenticatedIdentities": false,to:"allowUnauthenticatedIdentities": true,pushed to aws and it did the trick.allowUnauthenticatedIdentitiesseems not being updated after issuing amplify update api.found this: https://docs.aws.amazon.com/cognito/latest/developerguide/amazon-cognito-integrating-user-pools-with-identity-pools.html
worked for me…
Please check if you have configured your amplify app (as shown below) To know more visit this link
did anyone solve this? @jadbox @AntonSmatanik