amplify-js: Receiving {"message":"Unauthorized"} on API call
Do you want to request a feature or report a bug? Bug
What is the current behavior? The initialization looks like:
Amplify.configure({
Auth: {
mandatorySignIn: true,
region: config.cognito.REGION,
userPoolId: config.cognito.USER_POOL_ID,
identityPoolId: config.cognito.IDENTITY_POOL_ID,
userPoolWebClientId: config.cognito.APP_CLIENT_ID
},
API: {
endpoints: [
{
name: 'api_platform',
endpoint: config.apiGateway.URL,
region: config.apiGateway.REGION
}
]
}
});
I can successfully singin and get aws session with all the tokens. However, wen I run the following code
API.post('api_platform', '/ping');
I am getting {“message”:“Unauthorized”} .
When I pass the Authorization header
const options = {
headers: {
Authorization: "--token-"
}
}
API.post('api_platform', '/ping, options');
This works fine.
Is this expected behavior? Shell I pass Authorization header explicitly or the API should do that automaticly?
About this issue
- Original URL
- State: closed
- Created 6 years ago
- Reactions: 5
- Comments: 15 (1 by maintainers)
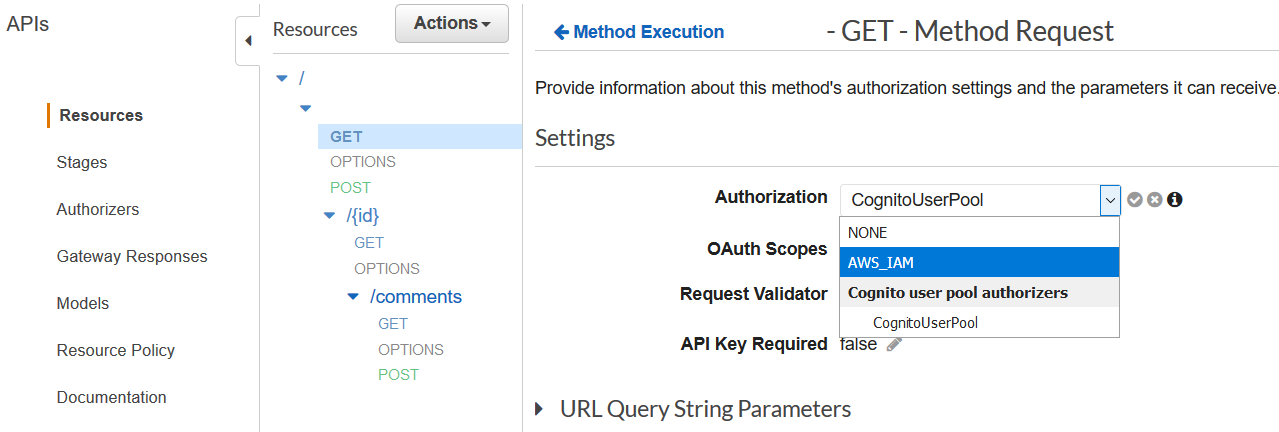
The documentation isn’t clear about that. If I understood well, Amplify use the Identity Pool token to sign the API requests. If you want to use this default behavior you need to use IAM Authorization in API Gateway and set the appropriate policy to the Identity Pool role.
To use the User Pool Authorizer you need to set the Authorization header with the User Pool token (like OP did).
I think Amplify should provide a way to choose between Identity Pool or User Pool for API request authentication.
This might help… you can configure it to use the IdToken JWT when defining your API endpoint
API: { endpoints: [ { name, endpoint, custom_header: async () => { // With Cognito User Pools use this: return { Authorization:Bearer ${(await Auth.currentSession()).getIdToken().getJwtToken()}} } } ] }yes except I think it should be
getIdToken(), I agree this could be close…I was just updating the comment so people might find this when looking for the problem@L226 I gave up with AWS_IAM configuration due to error:
{"message":"The request signature we calculated does not match the signature you provided. Check your AWS Secret Access Key and signing method. Consult the service documentation for details."}The final code that works for me is:
On each API Method Request settings.