amplify-js: Federated sign up doesn't set email_verified to true
Describe the bug
I am working on a React Native project.
When I sign up using Google I can successfully create an account but the property email_verified is not set which means that the app interprets the user as not verified.
Screenshots
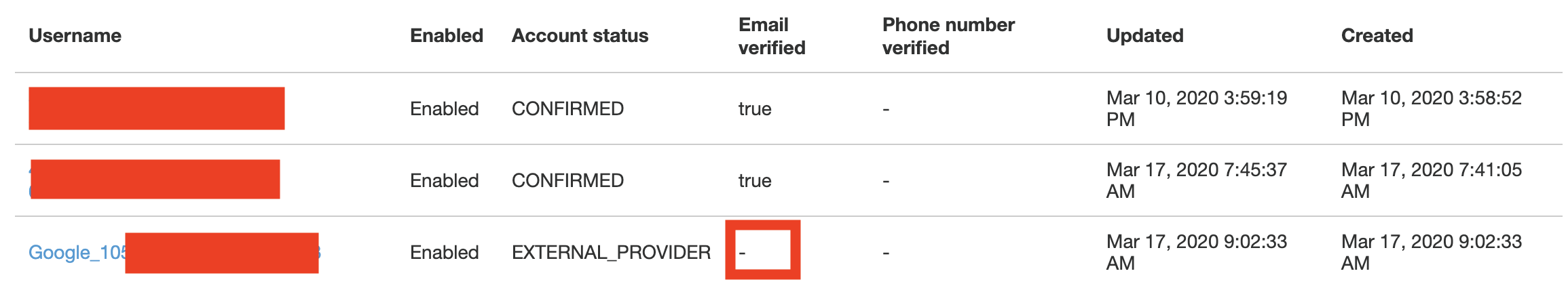
Environment
System:
OS: macOS 10.15.3
CPU: (12) x64 Intel(R) Core(TM) i7-8850H CPU @ 2.60GHz
Memory: 229.88 MB / 16.00 GB
Shell: 5.7.1 - /bin/zsh
Binaries:
Node: 12.11.0 - /usr/local/bin/node
Yarn: 1.19.2 - ~/.yarn/bin/yarn
npm: 6.11.3 - /usr/local/bin/npm
Watchman: 4.9.0 - /usr/local/bin/watchman
Browsers:
Chrome: 80.0.3987.132
Firefox: 72.0.2
Safari: 13.0.5
npmPackages:
@babel/core: ^7.6.2 => 7.8.3
@babel/runtime: ^7.6.2 => 7.8.3
@carimus/metro-symlinked-deps: ^1.1.0 => 1.1.0
@formatjs/intl-pluralrules: ^1.5.0 => 1.5.0
@formatjs/intl-relativetimeformat: ^4.5.7 => 4.5.7
@invertase/react-native-apple-authentication: ^0.1.1 => 0.1.1
@react-native-community/datetimepicker: ^2.2.2 => 2.2.2
@react-native-community/eslint-config: ^0.0.5 => 0.0.5
@react-native-community/masked-view: ^0.1.6 => 0.1.6
@react-native-community/netinfo: ^5.5.1 => 5.5.1
amazon-cognito-identity-js: ^3.2.5 => 3.2.5
aws-amplify: ^2.2.6 => 2.2.6
aws-amplify-react-native: ^3.2.2 => 3.2.2
babel-jest: ^24.9.0 => 24.9.0
date-fns: ^2.10.0 => 2.10.0
eslint: ^6.5.1 => 6.8.0
jest: ^24.9.0 => 24.9.0
metro-react-native-babel-preset: ^0.56.0 => 0.56.4
query-string: ^6.11.1 => 6.11.1
react: 16.9.0 => 16.9.0
react-intl: ^3.11.0 => 3.11.0
react-native: 0.61.5 => 0.61.5
react-native-device-info: ^5.4.1 => 5.4.1
react-native-gesture-handler: ^1.5.3 => 1.5.3
react-native-inappbrowser-reborn: ^3.3.4 => 3.3.4
react-native-linear-gradient: ^2.5.6 => 2.5.6
react-native-localize: ^1.3.2 => 1.3.2
react-native-modal: ^11.5.4 => 11.5.4
react-native-reanimated: ^1.7.0 => 1.7.0
react-native-safe-area-context: ^0.6.2 => 0.6.2
react-native-screens: ^2.0.0-alpha.25 => 2.0.0-alpha.25
react-native-spinkit: ^1.5.0 => 1.5.0
react-native-vector-icons: ^6.6.0 => 6.6.0
react-navigation: ^4.0.10 => 4.0.10
react-navigation-stack: ^2.0.15 => 2.0.15
react-navigation-tabs: ^2.7.0 => 2.7.0
react-test-renderer: 16.9.0 => 16.9.0
npmGlobalPackages:
@aws-amplify/cli: 4.16.0
@twilio/autopilot-cli: 0.0.27
undefined: 1.2.7
aws-amplify-monorepo: 0.1.30
gatsby-cli: 2.7.45
lighthouse: 4.2.0
nodemon: 1.18.7
npm: 6.11.3
sequelize-cli: 5.4.0
Smartphone (please complete the following information):
- Device: iPhone x
- OS: iOS 13.3.1
- Browser: inAppBrowser
Additional context It’s a React Native app.
About this issue
- Original URL
- State: closed
- Created 4 years ago
- Reactions: 2
- Comments: 28 (4 by maintainers)
@ionutmiftode I actually did! Its not the way I would have chosen in the first place, but for my app it actually works perfect:
The key is too use a “post confirmation trigger” and set the attribute through the AWS SDK itself (adminUpdateUserAttributes Method). The following code works for me:
What it does is: After the user authenticates successfully via federation, the post confirmation trigger is always invoked. At this point in time, the user fully exists within the user pool and can be updated through the AWS SDK for cognito. That means, that from within the Lambda function above, I use the cognito SDK itself to update the user and set the “email_verified”-Attribute through the adminUpdateUserAttributes()-Method. I do this only for federated users (user_status === EXTERNAL_PROVIDER), since I don’t want to mess with the already working post confirmation workflow for users that are registering via email. The trigger also seems to be updating the attribute through the SDK fast enough so that my App (React Native in my case) does not even try to send the user to the “verify email”-Screen. This is exactly the behavior I was hoping for. Keep in mind that your lambda execution role needs the “cognito-idp:AdminUpdateUserAttributes” permission to update the attributes through the SDK.
We rolled out this solution to production on May 10th and haven’t had any issues with it since and noticed around 30 user registrations via Facebook and Apple without any complaints.
While this is working I still don’t understand why we have to go this route. Having to verify the users email address if the users comes from a federated service does not make sense to me at all.
I hope this solution works for you as well! Feel free to contact me if you need any help 😃
I was running into the same problem because I didn’t notice that there is a “email_verified” attribute on Googles side to map to. This fixed my problems with the Google IDP, thank you!
But how do you set the email_verified attribute for Facebook, Apple or any other IDP that does not offer the email_verified attribute? I am currently implementing social logins into my React Native app using the Amplify HOC. Without the email_verified attribute, the user is always redirected to the verifyContact-Component where the confirmation code, which usually gets send via email, should be entered. Using social logins, this is not the desired behaviour.
I have not been able to find documentation on this when using federated logins and the amplify HOC. Any help would be very appreciated.
FYI @timoschlueter , @ionutmiftode :
So looks like our path forward is the right one (for now), and hopefully they move forward on the roadmap item at somepoint.
❤️
For those who discover this issue via Google, here are the related Cognito docs:
Example app:
@ionutmiftode , 😃 awesome
@timoschlueter , totally agree, a bunch of Cognito aspects seem unfinished (or atleast unpolished). I have a support case open with Amazon, if I get any headway there, I’ll update the thread.
Thank you so much!
FYI: @timoschlueter and @ionutmiftode
Real pain in the rear ❤️, Bradley
I ran into the same issue. I even tried using the pre-signup trigger with
autoVerifyEmailandautoVerifyPhoneset to true. That didn’t work either. @timoschlueter’s suggestion to use post-confirmation worked. Thanks!@HMilbradt Well It is not a Amplify bug directly BUT I agree completly with you about the stupidity of this.
Even when you use the presignup trigger with autoVerifyEmail to true, which is what we should do for this kind of tricks, it does not work… In this case it is literraly a bug (https://docs.amazonaws.cn/en_us/cognito/latest/developerguide/user-pool-lambda-pre-sign-up.html#aws-lambda-triggers-pre-registration-example-2) So here we are, we have to hack the given hack.
We currently “don’t” for Social. If a user logins with a native account, it will properly use the refreshToken to regain access as the user, but we hit a wall with Social, and our use case didn’t really require it, so if someone uses Social they just single click next time if logged out.
TY @slatted We ended up using both Post Authentication and Post Confirmation to solve the problem 😄
@slatted because of your finding I just checked our Cognito user pool and indeed found a few external users (< 10%) with email_verified still set to false. I haven’t noticed this before. Thanks for the info! I switched to a Post Authentication trigger as you suggested. Still seems to work as expected.
Really looks like a race condition.
I can’t stress this enough: The fact that we have to use such a hack in the first place is really frustrating. 😦
@timoschlueter used your solution, works as expected! I also fixed the profile picture issue here which is great!
One more thing, I added the logic in ‘Post Authentication’ lambda trigger, but this one is called when user sign in, not when he sign up, so I think the logic should be added in a Post Sign-up lambda trigger, but there is no such option.
the options from amplify cli for lambda trigger are:
Any idea which one I should use? Thanks
EDIT: So the winner is Post Confirmation 😄
@ionutmiftode unfortunately not. Our app uses just the email address 😦
@tim
Did you managed to verify the email address from facebook?
I have the same issue, using react native, google works fine but facebook requires an extra step to have the email verified
This issue has been automatically closed because of inactivity. Please open a new issue if are still encountering problems.
@elledienne Circling back, still waiting to hear from Amazon Cognito on this, apologizes on the delay.
@sammartinez Thanks a lot for your prompt answer, happy to support with testing/ experiment if that’s helpful 😃