aws-vault: secret-service gets: No such interface “org.freedesktop.DBus.Properties”
I am trying to use the secret-service backend on an Arch Linux installation. The desktop is a XDM session started via systemd.
When running
aws-vault --backend secret-service add example
I get
aws-vault: error: No such interface “org.freedesktop.DBus.Properties” on object at path /
I am not certain how to dig deeper. I have also installed libsecret and gnome-keyring. A hint where to look would be appreciated.
Thanks for the nice tool! The file backend works smoothly.
About this issue
- Original URL
- State: closed
- Created 6 years ago
- Reactions: 9
- Comments: 30 (1 by maintainers)
I am still hitting this. Running Ubuntu on Windows … Ubuntu 20.04 LTS (GNU/Linux 4.4.0-19041-Microsoft x86_64)
For anyone wanting to use aws-vault on headless WSL2 (or any headless linux system), I got it to work by using pass as the vault backend unstead of the default
gnome-keyring. Just install it and set it up with your GPG key using the instructions in the link, and set up these environment variables in your.bashrc(or.zshenv) or whatever:export AWS_VAULT_BACKEND=pass export AWS_VAULT_PASS_PREFIX=aws-vault export GPG_TTY=$(tty)
In my situation the root cause of the problem was with Vagrant. We can not use the SSH connection for the following command:
aws-vault add <name>, launching a terminal locally and executing the command will solve the problem. You must open a terminal on the machine itself.Resolution Steps: You have two possibilities to download the aws-vault. With brew and wget.
Recommended with brew:
brew install aws-vaultOr with wget:
Download AWS Vault
wget https://github.com/99designs/aws-vault/releases/download/v6.4.0/aws-vault-linux-amd64Install AWS Vault
Check AWS Vault version
aws-vault --versionDownload the pass and gnupg (used for encryption / decryption.)
sudo apt-get update && sudo apt-get install -y pass gnupgGenerates the key used for encryption / decryption.
gpg --gen-keyAfter generating the gpg key, you will get the output like in the example below:
Initialize the pass:
pass init "FD905667DE12B1678DF234272EEF7*********"AWS Vault profile creation Create a profile with any name and register the IAM user access key. After successful finishing previous point, you can create your aws-vault connection:
Check the created profiles.
aws-vault lsYou can use the AWS Vault profile you created to run AWS CLI commands.
aws-vault exec <your_profile_name>After creation the new terminal session, you can check the existing s3 buckets in your AWS:
aws s3 lsI ran into this issue too and I think I know why finally.
dbus-monitorwas super helpful here.aws-vault tries to create a secret collection named
awsvault. Creating a collection will normally cause gnome-keyring-daemon to pop-up a “prompt” dialog for setting a password on the new collection. But in a headless environment it can’t do this so it doesn’t register a Prompt provider on the path.If aws-vault instead used the default
logincollection it works fine because that collection already exists and is unlocked so no prompt is needed.I’m not sure if this is easily fixable in aws-vault because the collection name (as passed by the
ServiceNameattribute in thekeyring.Configstruct) is a fixed value. So this information is probably more useful for consumers of the https://github.com/99designs/keyring library.I’m looking for ways to create a collection from a commandline without needing to prompt and I’ll report back here if I find an existing tool for that
Same here. Ubuntu 20.04, WSL 2, 5.4.51-microsoft-standard-WSL2
Still broke on headless systems following suggestion above, you will need to open the x session and do this for the gnome keyring prompt. I think the keyring tool doesn’t support terminals at all, unfortunately.
this mirrors sovaradh’s findings and workaround using twm/xinitirc.
still gets
aws-vault: error: No such interface “org.freedesktop.DBus.Properties” on object at path /😕 Same for a native installation of POP_OS! 20.04 . But running
gnome-keyring-daemon -Vonce, then retryingaws-vault add myprofileagain prompted me to add a new keyring, and no error message again.I just had the same problem on a headless system.
Fix was to install a gnome desktop (on ubuntu 18.04
apt install ubuntu-mate-desktopwill do it) which runsgnome-keyring-daemonproperly.Once I logged into the desktop, the keyring, dbus and aws-vault stuff worked as expected.
I was able to run this from a SSH session to the box and was prompted by a passphrase dialog box within my X session:
I can log back out of the box and log in and
aws-vaultusessecret-servicefine.I’ve also run the same setup using kde and kwalletd.
Hope that helps.
@lucio-desimone-globant @lukeberry99 @murbanowicz I’ve tried using windows aws-vault in WSL, it doesn’t work. But I’ve got the WSL one working though.
what I’ve tried with windows aws-vault and may work for you:
But it doesn’t work for me when mfa is involved, throws another error for me
No luck with this error, also I don’t like this anyway because It uses credentials from windows file system instead of the ones from wsl. (If windows aws-vault works for you, you can set shared aws credentials env variables pointing to your WSL filesystem’s aws cred and config files.)
aws-vault throws the DBUS error on your WSL because gnome-keyring is a GUI application and WSL didn’t have GUI support before. Upon searching the internet a bit, I found that Microsoft released an update for WSL which adds GUI support. https://docs.microsoft.com/en-us/windows/wsl/tutorials/gui-apps#existing-wsl-install Run that update
after that install gnome-keyring (this might already be preset after WSL update but no harm in doing it)
sudo apt install gnome-keyringif you run your aws-vault command now it should work provided your abcd profile was set in ~/.aws/config file and respective credentials exist.
aws-vault exec abcd -- aws s3 lsif the prompt goes blank and you don’t see anything happen then kill gnome-keyring daemon and try again.
ps aux | grep "[g]nome-keyring-daemon" | awk '{print $2}' | xargs kill -9You should see a dialog pop up like this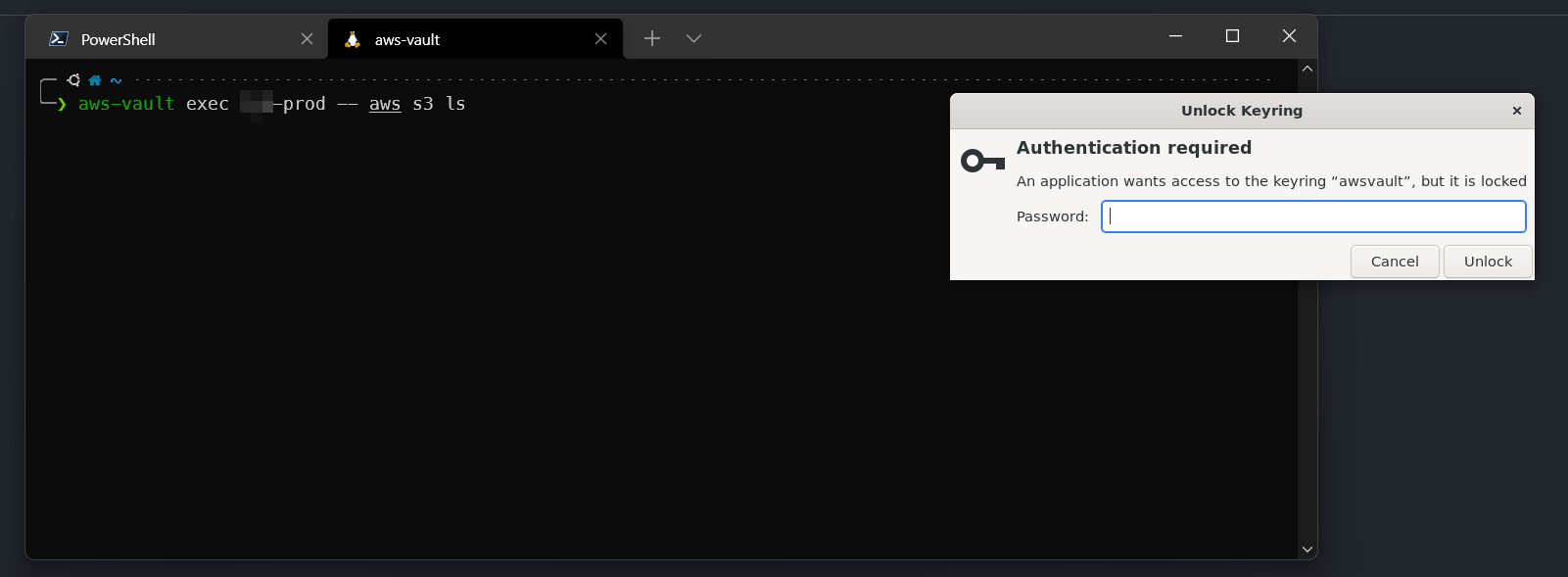
If your aws-vault command keeps spacing out, you have to kill the gnome-daemon everytime before running the aws-vault command. To avoid this I have edited the /usr/share/dbus-1/services/org.freedesktop.secrets.service file to look like this
I’m using a combo of aws-vault and assume-role so it doesn’t ask me the credentials every time. aws-vault sets a session and assume-role works until the session exists.
Hi there.
I’m using Ubuntu 20.04, WSL 2, 5.4.51-microsoft-standard-WSL2 as someone said in the comments.
Tried out all the possible solutions in the comments but nothing seems to work.
There might be a way to use the aws-vault from the host machine to add the profile and then try to execute the connection in the WSL container?
I’m stuck with this since a week.
Same issue. Ubuntu 18.04, I’ve ssh’ed into it, and
aws-vault add profilenamefails even if I try all the tips and tricks indicated above. Nothing works.This surfaces readily in Google searches for this issue, so adding what worked for me, taken from https://rtfm.co.ua/en/what-is-linux-keyring-gnome-keyring-secret-service-and-d-bus/: